Identity,
Information Security
Author:
Mark Dixon
Saturday, March 16, 2013
6:58 am
Oracle recently released a white paper entitled, “Oracle Access Manager Mobile and Social, A Case Study – Piggy Bank.”  This white paper outlines the use of the Mobile and Social component of the Oracle Access Management platform.  Mobile and Social provides a simple means to integrate Mobile applications with the security capabilities provided by Oracle’s Identity and Access Management platform.
The white paper:
discusses the effort involved in executing a Proof of Concept with a major international bank. While the PoC exercise was real and the requirements described in this paper implemented, certain details have been changed to protect the identity of the bank and its security architecture and simplified for those new to OAM Mobile and Social.
The Proof of Concept detailed in this white paper involved three main tasks:
- creating a simple electronic banking application
- the REST/JSON services for the application
- securing the application and services with the Oracle IAM technology stack.
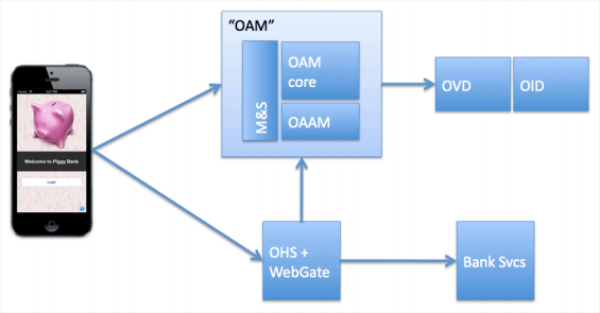
The “Piggy Bank” represents the bank for which the Proof of Concept was completed. Â The basic PoC architecture is shown below:
Â
The white paper does a good job of outlining just what is necessary to configure the components in this architecture.
The white paper concludes:
While the PiggyBank application is quite simple, it illustrates the power and capabilities of the Oracle Identity and Access Management platform including Oracle Access Manager, Oracle Adaptive Access Manager and some of the Mobile and Social Services. By using the OAM Mobile and Social SDK a fully functional mobile e-Banking application was created and secured in a very short time, without the need to install and configure any additional software and without the need to write complex code to secure the mobile App and its communication to the services it uses.Â
A customer with an existing security infrastructure based on Oracle Access Manager and Adaptive Access Manager can easily deploy Oracle Mobile and Social to extend the same security capabilities to mobile applications. By using the Mobile and Social SDK customers can seamlessly integrate security into their native Apps on popular mobile platforms including iOS and Android.
The need for secure mobile access is already huge and growing rapidly. Â The Oracle Mobile and Social product goes a long way towards meeting that demand.
Â
Â