Oracle and KPMG – Cloud Threat Report 2018

This morning, I was delighted to finally download and read the new “Oracle and KPMG – Cloud Threat Report 2018.† I have known this was coming for a few months, but was delighted by how it turned out.  The report contains a wealth of timely, insightful information for those who need to know how to not only cope, but excel, in the rapidly changing information systems infrastructures of modern business.
Mary Ann Davidson, CSO, Oracle Corporation, stated in the report’s Foreword:
In the age of social media, it is popular to speak of what’s “trending.†What we are seeing is not a trend, but a strategic shift: the cloud as an enabler of security.
The dazzling insights in the Oracle and KPMG Cloud Threat Report, 2018 come not from professional pundits, but from troops in the trenches: security professionals and decision makers who have dealt with the security challenges of their own organizations and who are increasingly moving critical applications to the cloud.
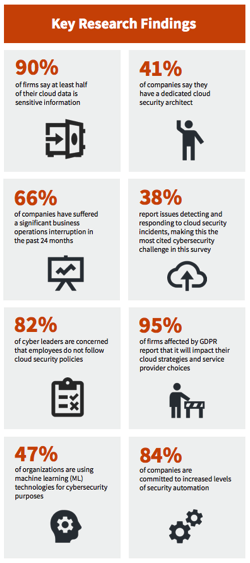
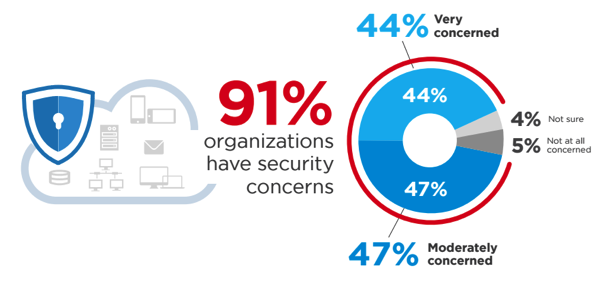
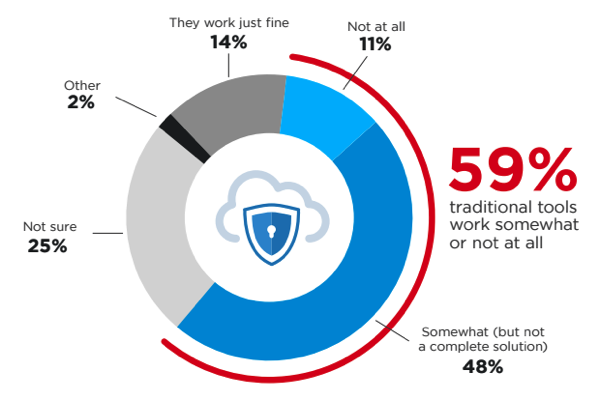
A few key research findings are summarized in the following list and illustrated by the numbers the “Key Research Findings” chart:
- The threat landscape is increasingly complex and varied.
- Detection and response is critical—but not always easy in the cloud.
- Customers don’t always understand their cloud security obligations.
- Security professionals worry about the impact of attacks on business operations.
- Cloud and mobile-centric employees beget the need for new identity and access management strategies.
- Technology alone isn’t enough.
- Machine learning can help.
KPMG offers this Call to Action:
C-level, finance, HR, risk, IT, and security leaders are responsible for ensuring that the organization has a cybersecurity program to address risks inherent in the cloud.
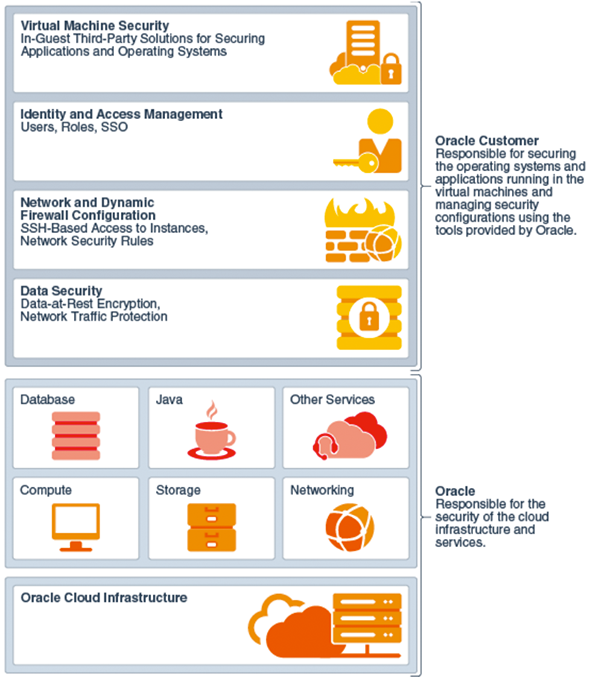
Beyond making sure that risks are mitigated and compliance requirements are addressed, leaders should accept and assert their responsibility for protecting the business. A critical first step is to understand the “shared responsibility†principles for cloud security and controls. Knowing what security controls the vendor provides allows the business to take steps to secure its own cloud environment.
To further protect an organization, it is crucial that everyone in the organization—not just its leaders—is educated about the cloud’s inherent risks and the policies designed to help guard against those risks. This requires clear communication and training to employees on cloud usage. KPMG and Oracle’s research found that there may be considerable room for improvement in this area, as individuals, departments, and lines of business within organizations are often in violation of cloud service policies.
I have really just skimmed the report. Â I look forward to digesting the content more completely. Â Stay tuned for more analysis and commentary from my perspective.