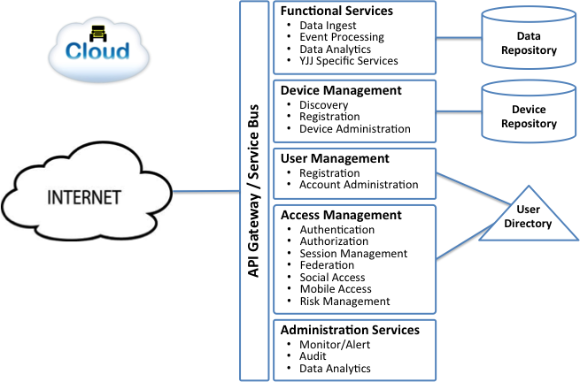
#YJJ Architecture: Services in the Cloud
On April 5th, I posted a high level architecture diagram of sensors, subsystem controllers, gateway and supporting functions that will need to exist on the Jeep.  Today’s post offers a high level diagram of functionality that should exist in the Yellow Jeep Cloud. This roughly follows the structure of the Oracle IoT Platform I described in my March 22nd post.
Â
One basic design objective is that all functions will be exposed as secure API’s that could be consumed by web apps or mobile apps as needed.  Therefore, the primary interface to the open Internet is a secure API gateway.  This may operate in conjunction with an enterprise service bus that manages a catalog of available services and API’s.
For the purpose of this post, available services are divided into five major categories, with three major data repositories:
First, the data repositories:
Data Repository. Â This is the database where all data from the Jeep (or many Jeeps) will be collected and stored for functional processing or analysis.
Device Repository. Â This database will be used to maintain a complete catalog of all available and used devices, along with capabilities pertaining to each device.
User Directory.  This directory will be used to maintain all users, access rights and credentials necessary to access data services and applications in the YJJ cloud.
Now, the functional elements:
Functional Services. Â These services are really the focal point of the YJJ cloud. Â It is this functionality that will make the the data collected and used from the Jeeps used. Â Some functions may be quite generic, such as data ingest, event processing and data analytics, but I anticipate that a set of #YJJ-specifc services (yet to be defined) will be the most important set of functions in this group.
Device Management. Â A complete catalog of devices authorized to connect to the YJJ Cloud will need to be maintained, and secure access rules enforced. Â Functions to discover, register and manage changes to this large network of devices will be required.
User Management. Â All users that will access YJJ data, services, APIs or applications will need to be registered and access rights be appropriately granted. Â
Access Management. Access Management or Control functionality will be needed to enforce security polity for application access by users as well as to secure the APIs that can be used by external applications for accessing YJJ functionality.
Administration Services. Â Common administration services will be needed to monitor the health of system components and provide auditing and reporting functions.
This provides a very high level view of my thoughts for YJJ Cloud functionality. Â Much more definition is needed for each set of services. Â Stay tuned!
Roll on Yellow Jeep Journey!
Â