This week, I read an interesting report created by the Top Threats Working Group of the Cloud Security Alliance and sponsored by Hewlett Packard. Entitled, “The Treacherous Twelve: Cloud Computing Top Threats in 2016,†this report points out that new security vulnerabilities are emerging …
the improved value offered by cloud computing advances have also created new security vulnerabilities, including security issues whose full impacts are still emerging.
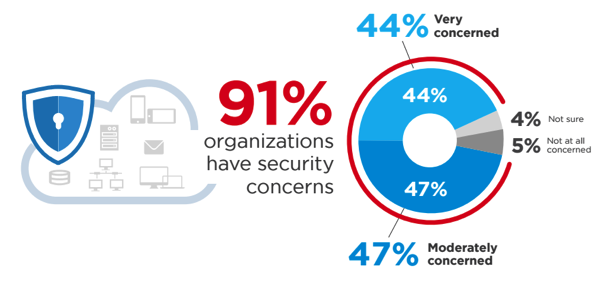
… and that security is no longer just an IT issue.Â
The 2016 Top Threats release mirrors the shifting ramifications of poor cloud computing decisions up through the managerial ranks. Instead of being an IT issue, it is now a boardroom issue.
More vulnerabilities and increased business awareness/responsibility. The urgency of security is rising.
The report identifies security concerns so business leaders can make better decisions about security:
The purpose of the report is to provide organizations with an up-to-date, expert-informed understanding of cloud security concerns in order to make educated risk management decisions regarding cloud adoption strategies. The report reflects the current consensus among security experts in CSA community about the most significant security issues in the cloud.
The 12 critical issues to cloud security (ranked in order of severity per survey results):
- Data Breaches
- Weak Identity, Credential and Access Management
- Insecure APIs
- System and Application Vulnerabilities
- Account Hijacking
- Malicious Insiders
- Advanced Persistent Threats (APTs)
- Data Loss
- Insufficient Due Diligence
- Abuse and Nefarious Use of Cloud Services
- Denial of Service
- Shared Technology Issues
The report provides includes a variety of useful information about each critical issue, including:
- Description
- Business Impact
- Anecdotes and Examples
- List of applicable controls from the Cloud Control Matrix (CCM)
- Links to further information
Some of the anecdotes are both intriguing and disturbing:
British telecom provider TalkTalk reported multiple security incidents in 2014 and 2015, which resulted in the theft of four million customers’ personal information. The breaches were followed by a rash of scam calls attempting to extract banking information from TalkTalk customers. TalkTalk was widely criticized for its failure to encrypt customer data.
Praetorian, an Austin, Texas-based provider of information security solutions, has launched a new cloud-based platform that leverages the computing power of Amazon AWS in order to crack password hashes in a simple fashion.
Heartbleed and Shellshock proved that even open source applications, which were believed more secure than their commercial counterparts … , were vulnerable to threats. They particularly affected systems running Linux, which is concerning given that 67.7% of websites use UNIX, on which the former (Linux) is based.
In June 2014, Code Spaces’ Amazon AWS account was compromised when it failed to protect the administrative console with multifactor authentication. All the company’s assets were destroyed, putting it out of business.
The threat is real, folks. Â Be careful out there!