Today I read a year-old document published by Gartner, entitled, “The Nexus of Forces: Social, Mobile, Cloud and Information.” Â It explains the interaction among these market forces better than any single document I have read:
Research over the past several years has identified the independent evolution of four powerful forces: social, mobile, cloud and information. As a result of consumerization and the ubiquity of connected smart devices, people’s behavior has caused a convergence of these forces.
In the Nexus of Forces, information is the context for delivering enhanced social and mobile experiences. Mobile devices are a platform for effective social networking and new ways of work. Social links people to their work and each other in new and unexpected ways. Cloud enables delivery of information and functionality to users and systems. The forces of the Nexus are intertwined to create a user-driven ecosystem of modern computing. (my emphasis added)
Excerpts from Gartner’s treatment of each of these areas include:
Social
Social is one of the most compelling examples of how consumerization drives enterprise IT practices. It’s hard to think of an activity that is more personal than sharing comments, links and recommendations with friends. Nonetheless, enterprises were quick to see the potential benefits. Comments and recommendations don’t have to be among friends about last night’s game or which shoes to buy; they can also be among colleagues about progress of a project or which supplier provides good value. Consumer vendors were even quicker to see the influence — for good or ill — of friends sharing recommendations on what to buy.
Mobile
Mobile computing is forcing the biggest change to the way people live since the automobile. And like the automotive revolution, there are many secondary impacts. It changes where people can work. It changes how they spend their day. Mass adoption forces new infrastructure. It spawns new businesses. And it threatens the status quo.
Cloud
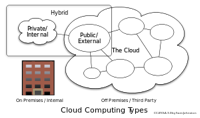
Cloud computing represents the glue for all the forces of the Nexus. It is the model for delivery of whatever computing resources are needed and for activities that grow out of such delivery. Without cloud computing, social interactions would have no place to happen at scale, mobile access would fail to be able to connect to a wide variety of data and functions, and information would be still stuck inside internal systems.
Information
Developing a discipline of innovation through information enables organizations to respond to environmental, customer, employee or product changes as they occur. It will enable companies to leap ahead of their competition in operational or business performance.
Gartner’s conclusion offers this challenge:
The combination of pervasive mobility, near-ubiquitous connectivity, industrial compute services, and information access decreases the gap between idea and action. To take advantage of the Nexus of Forces and respond effectively, organizations must face the challenges of modernizing their systems, skills and mind-sets. Organizations that ignore the Nexus of Forces will be displaced by those that can move into the opportunity space more quickly — and the pace is accelerating.
So, what does this mean for Identity and Access Management? Â Just a few thoughts:
- While “Social Identity” and “Enterprise Identity” are often now considered separately, I expect that there will be a convergence, or at least a close interoperation of, the two areas. The boundaries between work and personal life are being eroded, with work becoming more of an activity and less of a place. Â The challenge of enabling and protecting the convergence of social and enterprise identities has huge security and privacy implications.Â
- We cannot just focus on solving the IAM challenges of premised-based systems. Â IAM strategies must accommodate cloud-based and premise-based systems as an integrated whole. Â Addressing one without the other ignores the reality of the modern information landscape.
- Mobile devices, not desktop systems, comprise the new majority of user information tools. IAM systems must address the fact that a person may have multiple devices and provide uniform means for addressing things like authentication, authorization, entitlement provisioning, etc. for use across a wide variety of devices.
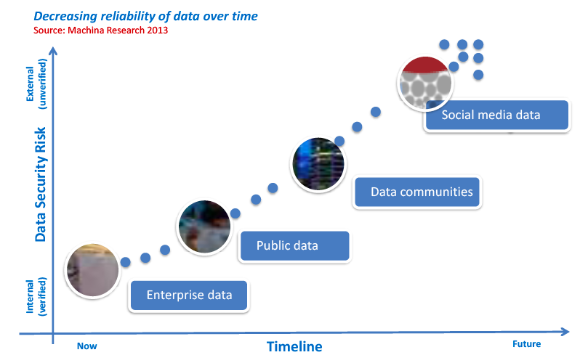
- We must improve our abilities to leverage the use of the huge amounts of information generated by mobile/social/cloud platforms, while protecting the privacy of users and the intellectual property rights of enterprises.
- Emerging new computing paradigms designed to accommodate these converging forces, such as personal clouds, will require built-in, scalable, secure IAM infrastructure.
- The Gartner Nexus doesn’t explicitly address the emergence of the Internet of Things, but IoT fits well within this overall structure. Â The scope of IAM must expand to not only address the rapid growth of mobile computing devices, but the bigger virtual explosion of connected devices.
We live in an interesting time. The pace of technological and social change is accelerating. Wrestling with and resolving IAM challenges across this rapidly changing landscape is critical to efforts to not only cope with but leverage new opportunities caused by these transformative forces.