#IoT, Big Data and Authenticity
Today, I read an interesting white paper, “Big Data in M2M: Tipping Points and Subnets of Things,” published by Machina Research. From the introduction:
This White Paper focuses on three hot topics in the TMT space currently: Big Data and the ‘Internet of Things’, both examined through the prism of machine-to-machine communications. We have grouped these concepts together, since Big Data analytics within M2M really only exists within the context of heterogeneous information sources which can be combined for analysis. And, in many ways, the Internet of Things can be defined in those exact same terms: as a network of heterogeneous devices.
The white paper does a good job of exploring the emerging trends of the Internet of Things, potential business opportunities and challenges faced.
As one could expect, “authenticity and security of different kinds of data,” was identified as a big challenge:
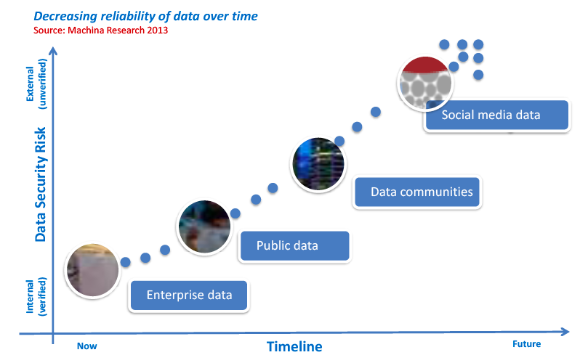
Big Data is about “mashing up†data from multiple sources, and delivering significant insights from the data. It is the combination of data from within the enterprise, from openly available data (for example, data made available by government agencies), from data communities, and from social media. And with every different source of data arises the issues of authenticity and security. Machina Research predicts that as a result of the need for data verification, enterprises will have a greater inclination to process internal and open (government) data prior to mashing-up with social media.
The following diagram shows the increase security risk as more data from external sources is collected and analyzed.
This yet another indicator of how Identity and Access Management will be critical in the successful evolution of the Internet of Things.