Turing Test (Reversed)
The classic Turing Test, according to Wikipedia, is:
a test of a machine’s ability to exhibit intelligent behavior equivalent to, or indistinguishable from, that of a human. Alan Turing proposed that a human evaluator would judge natural language conversations between a human and a machine that is designed to generate human-like responses. …
The test was introduced by Turing in his 1950 paper “Computing Machinery and Intelligence.†…
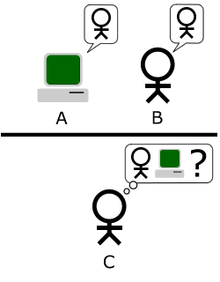
As illustrated in the first diagram:
The “standard interpretation” of the Turing Test, in which player C, the interrogator, is given the task of trying to determine which player – A or B – is a computer and which is a human. The interrogator is limited to using the responses to written questions to make the determination. …
In the years since 1950, the test has proven to be both highly influential and widely criticised, and it is an essential concept in the philosophy of artificial intelligence.
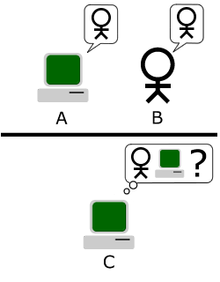
What if the roles were reversed, and a computer was tasked with determining which of the entities on the other side of the wall was a human and which was a computer?  Such is the challenge for software that needs to decide which requests made to an online commerce system are generated by humans typing on a browser, and which are illicit bots imitating humans.
By one year-old estimate, “more than 61 percent of all Web traffic is now generated by bots, a 21 percent increase over 2012.†Computers must automatically determine which requests come from people and which come from bots, as illustrated in the second diagram.
While this is not strictly a Turing test, it has some similar characteristics.  The computer below the line doesn’t know ahead of time what techniques the bots will use to imitate human interaction. These decisions need to be made in real time and be accurate enough to prevent illicit bots from penetrating the system. A number of companies offer products or services that accomplish this task.
One might ask, “Does this process of successfully choosing between human and bot constitute artificial intelligence?”
At the current state of the art, I think not, but it is area where enhanced computer intelligence could provide real value.