Time for a Federal Data Breach Law in the US?

Recently, I have given several presentations about the European Union’s General Data Protection Regulation (GDPR). A common question that arises is whether we should expect a similar data protection regulation in the US. Â
This morning, an interesting article on the subject crossed my desk: “No more waiting: it’s time for a federal data breach law in the U.S.”
A few excerpts:
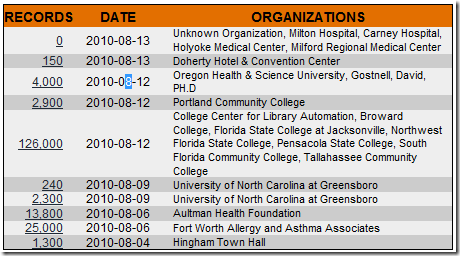
With the recent passage of data breach notification laws in Alabama and North Dakota, all U.S. states and the District of Columbia now require that companies let us know when our personal data are breached. It only took 15 years.
Notably, states overwhelmingly require notification only if some sort of financial data or password information is involved. That’s a problem because data breaches often entail other kinds of harm. A better, more rights-respecting standard — one that could be incorporated into existing state standards and a new federal law — would require companies to notify us of breaches of our personal information tied to other harms.
It is crucial that any new federal standard does not prevent states from adding protections. A federal breach law should create a floor of minimum standards that companies must meet, not a ceiling prohibiting tougher state enforcement.
Members of Congress have already proposed a number of data breach notification laws, but while some proposals are better than others, none have been great for the people these laws are supposed to protect. Even one of the better efforts had provisions to preempt stronger state laws. As we wait for the right bill, ordinary people remain vulnerable and without sufficient redress under many state laws.
It seems to me that demand in the US for privacy protection in general and breach notification in particular has lagged such demand in Europe, probably because of difference in culture and political philosophy. Â However, due to the increaser in high-profile data breaches in the last couple of years, I expect we will see federal legislation fairly soon.Â
Â


 The recent security breach affecting Sony Corp’s PlayStation network, is receiving high profile attention. As reported by Nick Wingfield in today’s
The recent security breach affecting Sony Corp’s PlayStation network, is receiving high profile attention. As reported by Nick Wingfield in today’s