What is more valuable – linkages between web pages or between people?
I was intrigued by a headline I read this morning, “How Facebook Can Put Google Out of Business,” by Ben Elowitz (@elowitz), co-founder and CEO of Wetpaint.
Elowitz started by stating his admiration for Google:
I used to envy Google and the vast digital empire that Schmidt commanded. Â Google had one of the most intricate monopolies of all time. It had the most impressive dataset the world had ever seen; the most sophisticated algorithm to make sense of it; an audience of a billion users expressing their interest; and more than a million advertisers bidding furiously to reach those consumers at just the right moment.
What’s more, it had captured the ultimate prize: increasing returns to scale. Only Google could spread such huge R&D costs among an even more humongous query volume, all while offering advertisers the chance to reach most of the population with one buy. Google had earned its success.
However, he as concluded that Facebook offers more inherent value than Google, and can beat Google at its own game:
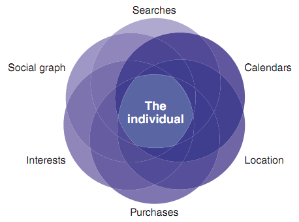
While Google has amassed an incredible database consisting of the fossilized linkages between most Web pages on the planet, Facebook possesses an asset that’s far more valuable—the realtime linkages between real people and the Web.What does this mean, and what are the implications here?
Well, in a nutshell, Facebook has stored a treasure trove of distinctive data that, if fully utilized, could put Google out of business.
I’m not astute enough to predict whether Facebook or Google will win, but I believe Elowitz has identified an important distinction between the inherent value of linkages:
“linkages between real people and the Web” [and, I might add, linkages between real people] – Â primary Facebook value
or
“linkages between Web pages” – primary Google value
 We call linkages between people “relationships”. In my previous post, each line on my LinkedIn connection map represents a real life relationship. Some of my Linkedin relationships are closer in real life than others, just like some of my Facebook “friendships” are closer than others. Â But they are real. Â They do exist.
We call linkages between people “relationships”. In my previous post, each line on my LinkedIn connection map represents a real life relationship. Some of my Linkedin relationships are closer in real life than others, just like some of my Facebook “friendships” are closer than others. Â But they are real. Â They do exist.
My real-life relationships represented by Facebook or LinkedIn have inherent value to me. Â Both Facebook and LinkedIn provide real value to me through the services they provide.
Google has proven that there is great business value in “linkages between web pages”. Â I believe companies like Facebook and LinkedIn are beginning to how to business value can be derived from “linkages between people”. Â Google is clearly trying to catch up in the relationships business, where Eric Schmidt admits they have failed.
It will be interesting to see how they, and other companies of their ilk, will continue to succeed for fail in business as they leverage (in a positive sense) their understanding of my relationships, hopefully without exploiting (in a negative sense), the private information I entrust to them.

 When I hear a message that begins, “We’re from the government, and we’re here to help,” I am naturally suspicious. My political philosophy, based on personal freedom, individual responsibility and natural consequences, is all too often infringed upon by over-reaching, even if well-intentioned, government mandates. So, when I first learned of the “
When I hear a message that begins, “We’re from the government, and we’re here to help,” I am naturally suspicious. My political philosophy, based on personal freedom, individual responsibility and natural consequences, is all too often infringed upon by over-reaching, even if well-intentioned, government mandates. So, when I first learned of the “ It was almost two months ago when I
It was almost two months ago when I 


