Identity,
Social Media
Author:
Mark Dixon
Thursday, February 24, 2011
10:44 am
I recently stumbled across an interesting site, Klout.com, which analyzes a Twitter account’s history and assigns a “Klout Score,†which is purported to be a “measurement of your overall online influence.
Of course, my inquisitive nature as it is, I had to try it for my Twitter account, @mgd. The results were not great, but respectable, I suppose:
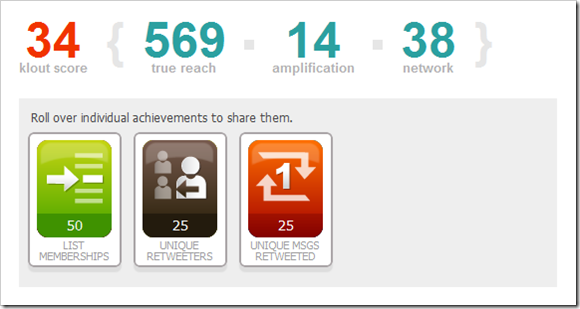
By contrast, the Klout Score of my favorite Phoenix Suns tweeter, Jared Dudley, was 70.
The three major components of the score are:
- True Reach – the real size of your engaged audience.
- Amplification Probability – the likelihood that your content will be acted upon.
- Network Influence – the influence level of your engaged audience.
Additionally, Klout offered a categorization for my twitter account.
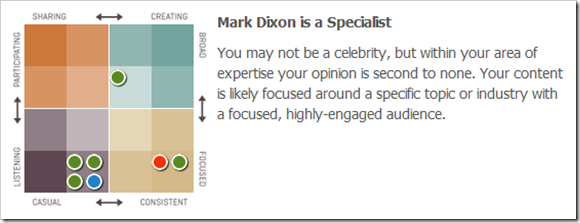
I am certainly not a celebrity, but I do try to be consistent and focused. I have a small number of followers who seem to be fairly well engaged.
For example, after I had received my Klout store, I joked on Twitter,
“Let’s hope that low @Klout doesn’t mean low worth.â€
An “engaged†Twitter follower responded with this encouraging note:
“@mgd I’m sure our worth as human beings is not related to Klout. :)â€
That was certainly good news. I am glad that my intrinsic worth really isn’t dependent on my Twitter Klout score. I was reminded of the profound observation printed on a framed picture my wife gave me many years ago:
“In a hundred years from now it will not matter what my bank account was, the type of house I lived in, or the kind of clothes I wore. But the world may be much different, because I was important in the life of a child.â€
The bottom line? Klout is interesting, but has little to do with my value as a human being and the impact I can make on things that really matter.
Technorati Tags:
Klout,
Value,
Worth







 Malicious hackers who may be based in China managed to fool Canadian federal IT staff into providing access to government computers, leading to severe Internet restrictions at Treasury Board and the Finance Department. …
Malicious hackers who may be based in China managed to fool Canadian federal IT staff into providing access to government computers, leading to severe Internet restrictions at Treasury Board and the Finance Department. …