Oracle White Paper: Information Security – A Conceptual Architecture Approach
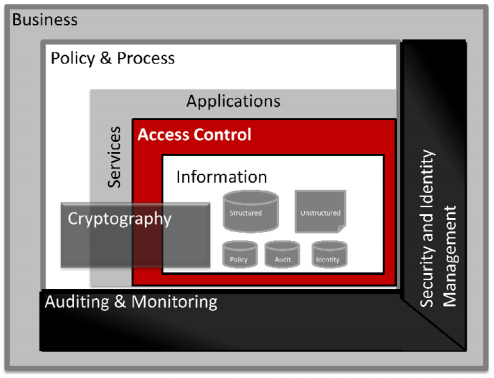
Information Security is a strategic approach that should be based on a solid, holistic framework encompassing all of an organization’s Information Security requirements, not just those of individual projects. The framework should be based on a reference architecture that takes into account key security principles such as ‘Defence in Depth’ and ‘Least Privileges’. By taking this approach to Information Security, organizations can ensure that the components of their Information security architecture address all business critical Information and are driven by the requirements of the business.
Our aim is to discuss the importance of providing an end-to-end, defence in depth enterprise-wide Information Security architecture with practical proof points, to meet both business and IT requirements for control as well as enabling the organisation to meet their desired goals.
- Information Security Architecture Requirements
- Information Security Conceptual Architecture
- Validation of the Architecture
The paper addresses issues from business policy to technology enablers, effectively showing how information security can support enterprise business objectives and processes. Thank you, Paul, for providing this excellent white paper.




 Malicious hackers who may be based in China managed to fool Canadian federal IT staff into providing access to government computers, leading to severe Internet restrictions at Treasury Board and the Finance Department. …
Malicious hackers who may be based in China managed to fool Canadian federal IT staff into providing access to government computers, leading to severe Internet restrictions at Treasury Board and the Finance Department. …


