Enterprise Architecture,
Identity,
Information Security
Author:
Mark Dixon
Tuesday, December 20, 2011
10:10 am
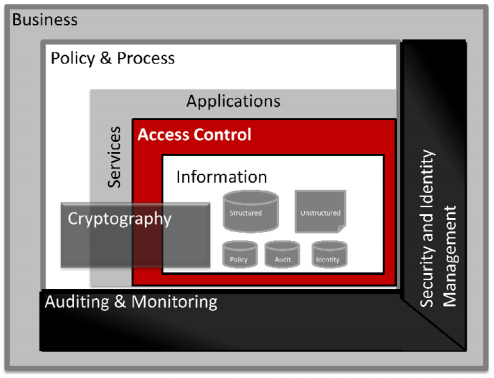
 The Oracle outward-facing website is a virtual cornucopia of valuable information. Â Unfortunately, I often just stumble onto valuable gems of knowledge instead of discovering them in an organized fashion. Â Today was such a case. Â Quite by accident, I found an excellent overview of Information Security issues in “Information Security, A Conceptual Architectural Approach.” Â It provides, in an easy-reading 25 pages, a good overview of information security principles and approaches to addressing them.
The Oracle outward-facing website is a virtual cornucopia of valuable information. Â Unfortunately, I often just stumble onto valuable gems of knowledge instead of discovering them in an organized fashion. Â Today was such a case. Â Quite by accident, I found an excellent overview of Information Security issues in “Information Security, A Conceptual Architectural Approach.” Â It provides, in an easy-reading 25 pages, a good overview of information security principles and approaches to addressing them.
This document referenced a larger treatise, the Oracle Reference Architecture – Security, which dives more deeply into information security issues and solutions. Â In about 130 pages, this reference architecture document provides an excellent treatment of the basic principles of information security and recommended approaches to mitigate security risk. Â The introduction aptly states:
Information is the lifeblood of every organization. If this Information is compromised there can be a wide range of consequences ranging from damage to a company’s reputation through to financial penalties such as regulatory fines and cost of remediation. …
Information Security is a strategic approach that should be based on a solid, holistic framework encompassing all of an organization’s Information Security requirements, not just those of individual projects. …
By taking this approach to Information Security, organizations can ensure that the components of their Information security architecture address all business critical Information and are driven by the requirements of the business.
The document is organized as follows:
- Introduction to Information Security
- Security Concepts and Capabilities
- Common Security Standards
- Conceptual Architecture View
- Logical View
- Product Mapping View
- Deployment View
- Summary
I hope you will find this to be a useful reference.