Perspectives on Identity and Cloud Computing
 Dave Kearns indentified three separate focus areas for Identity and Cloud Computing in his Network World post today:
Dave Kearns indentified three separate focus areas for Identity and Cloud Computing in his Network World post today:
Identity-in-the-cloud, or Identity as a Service:
IdM services such as provisioning, governance, role management, compliance, etc. are hosted "in the cloud."
Identity-for-the-cloud:
Provisioning services for cloud apps provided by traditional, on-premise, provisioning vendors as well as other identity services (privileged user management, compliance, etc.) extended to the cloud from your data center.
Meshed, or integrated, on-premise/in-the-cloud:
Linking on-premises Identity Management infrastructure and cloud identity data from cloud-hosted applications.
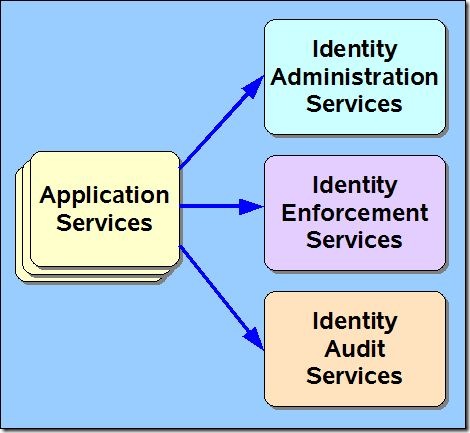
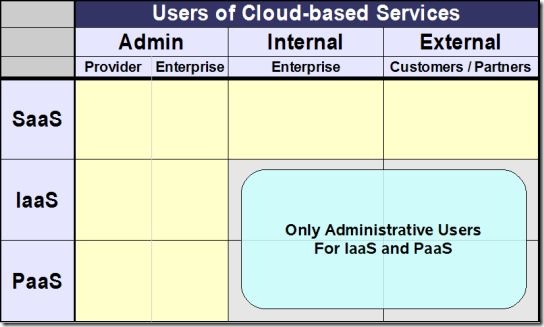
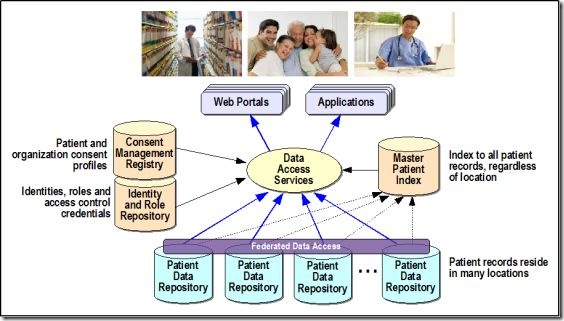
More than anything, this points out that Identity Management and Cloud Computing is a multi-faceted issue. “Cloud†may refer to where the Identity Management services are hosted, as well as where the applications reside that consume Identity Management services – or a combination of both.
Certainly worth further exploration.