Apollo – the VBOF Stork
My blogging efforts have been on an extended hiatus recenlty as I have focused on becoming familiar with the new Oracle landscape. Perhaps there is no better way to return to the blogosphere than to announce the winner of the Sun VBOF Stork naming contest.
A bit of explanation is in order …
In December and January, I hosted a short-lived series of “Virtual Birds of a Feather†(VBOF) sessions, held via teleconference and Webex. These sessions, which were open to Sun employees and SI partners, covered such interesting topics as:
- Identity Roles and Personae
- Current Trends and Issues around Entitlements Certification
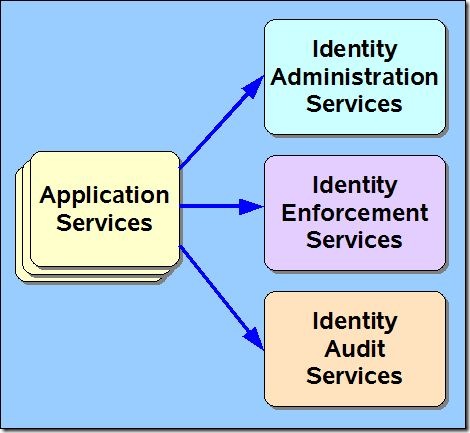
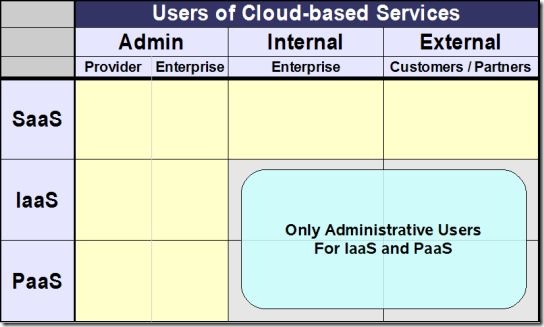
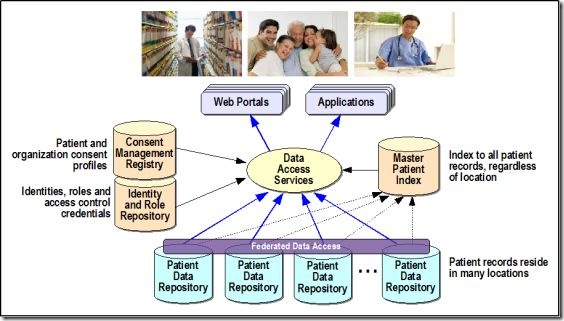
- Identity and Access Management in Cloud Computing
We had people from literally around the world participating in these live sessions, and collectively learned much through cooperative discussion of Identity Management topics.
As I was searching for an appropriate artwork to use for VBOF presentations, I stumbled across a photo of a gallant old stork in the Sun artwork collection. We adopted the old bird as the VBOF mascot and launched a little election to determine what to name him.
The winning name was nominated by Dr. Rene Klomp, Senior Solution Architect from the Netherlands, who suggested that Apollo is:
“God of the Sun, who had an Oracle in Delphi. Also ‘Apollo’ can be read ‘a pollo’ which means ‘a chicken’ which is of course a virtual stork! Oh well, they’re both birds so what the heck. Last but not least, Apollo took us to the moon, which gives us light after the Sun has set.â€
Today, I finally received a photo of Rene wearing the one and only Apollo/VBOF shirt, which he received as winner of our little contest.
Congratulations to Rene for both nominating the winning name and wearing the shirt so stylishly!
I don’t know yet whether we’ll revive the VBOF concept within Oracle, but if we do, I’m sure Apollo the VBOF Stork will be waiting in the wings.


 Mail
Mail