 I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “Secret iPhone Feature Tracks Owners’ Whereabouts“:
I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “Secret iPhone Feature Tracks Owners’ Whereabouts“:
Security researchers have discovered a hidden iPhone feature that secretly tracks and saves the meanderings of the phone – and presumably its owner.
The tracking feature was described in a presentation at the Where 2.0 Conference in San Francisco on Wednesday. According to the researchers, Pete Warden, founder of Data Science Toolkit and Alasdair Allan a researcher at Exeter University in the UK, the tracking feature records the phone’s movements, including what cell phone towers and Wifi hotspots it connects to, when and where. While that information isn’t shared with Apple, it is retained even when iPhone users update their hardware, suggesting that Apple had plans to use the data at a later time.
Was I surprised? No. Irritated? Yes. We have one more piece of evidence, that when power is concentrated in the hands of a few, abuses tend to occur.
After reading the O’Reilly Radar article, “Got an iPhone or 3G iPad? Apple is recording your moves“, I followed a link to an application to see for myself:
How can you look at your own data?
We have built an application that helps you look at your own data. It’s available at petewarden.github.com/iPhoneTracker along with the source code and deeper technical information.
The broad view clearly showed the four states in which I have used my month-old iPad:
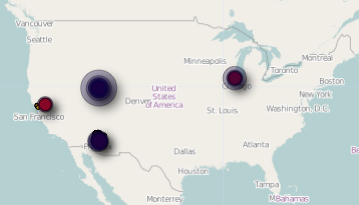
But the real interesting view was of my supposed meanderings in Arizona:
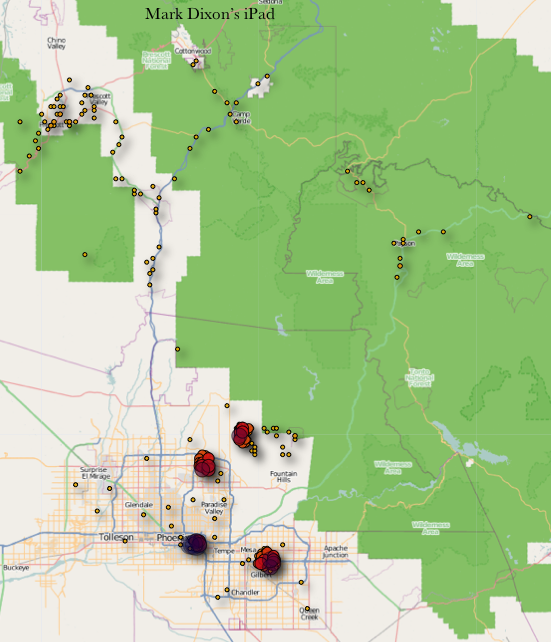
I can easily explain three of the four major clumps of usage in the Phoenix metropolitan area – my home, the Phoenix airport, and a client site. But I have never taken my iPad to the fourth area of supposed heavy use.
All the outliers are even more problematic. I used the iPad once in a mountainous area northeast of Phoenix, but all the other outliers? My only explanation is that I must have forgotten to place the iPad in “Airplane Mode” on one or more more of my flights (heaven forbid!). The iPad must have connected with dozens of cell towers as we flew over.
My message to Steve Jobs? Please, just call. I’d gladly invite you over for dinner or take you to my favorite restaurant, where we could discuss the things that are important to me in my life. But these shenanigans? Really tawdry for a supposely high class company.


 I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “
I first read the news about Apple’s secretive location tracking capability in the Kaspersky Labs Threat Post article, “


 Mail
Mail