Information Security in the Oil and Gas Critical Infrastructure Protection (CIP) Sectors
In a recent post, I highlighted a new Oracle white paper entitled, “Protecting the Electric Grid in a Dangerous World,†which describes how Oracle Identity Management solutions and the Oracle data security portfolio offer an effective, defense-in-depth security strategy to help meet this challenge, playing a key role in the North American Energy Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) cyber security standards.
 An Oracle colleague asked appropriately, What about the oil and gas industry? Isn’t this part of the energy industry also considered part of the critical infrastructure in the United States? Isn’t the oil and gas industry vulnerable to cyber attack? Aren’t methods for protecting information assets in the oil and gas industry similar to those in the electrical distribution industry?
An Oracle colleague asked appropriately, What about the oil and gas industry? Isn’t this part of the energy industry also considered part of the critical infrastructure in the United States? Isn’t the oil and gas industry vulnerable to cyber attack? Aren’t methods for protecting information assets in the oil and gas industry similar to those in the electrical distribution industry?
The answer to each question is a resounding “Yes,†but with some differences. Let’s explore a bit of history and discuss the focus of Information Security in the Oil and Gas Critical Infrastructure. This post is longer than most of my blog posts, but I felt the length was justified to give a good overview of the topic.
Historical Perspective
 The Federal Government official recognition of the vulnerability of critical infrastructure in the US began with the Presidential Decision Directive NSC-63 on Critical Infrastructure Protection, signed by Bill Clinton on May 22, 1988. The executive summary of that directive reads in part:
The Federal Government official recognition of the vulnerability of critical infrastructure in the US began with the Presidential Decision Directive NSC-63 on Critical Infrastructure Protection, signed by Bill Clinton on May 22, 1988. The executive summary of that directive reads in part:
The United States possesses both the world’s strongest military and its largest national economy. Those two aspects of our power are mutually reinforcing and dependent. They are also increasingly reliant upon certain critical infrastructures and upon cyber-based information systems.
Critical infrastructures are those physical and cyber-based systems essential to the minimum operations of the economy and government. They include, but are not limited to, telecommunications, energy, banking and finance, transportation, water systems and emergency services, both governmental and private. Many of the nation’s critical infrastructures have historically been physically and logically separate systems that had little interdependence. As a result of advances in information technology and the necessity of improved efficiency, however, these infrastructures have become increasingly automated and interlinked. These same advances have created new vulnerabilities to equipment failure, human error, weather and other natural causes, and physical and cyber attacks. Addressing these vulnerabilities will necessarily require flexible, evolutionary approaches that span both the public and private sectors, and protect both domestic and international security.
The Homeland Security Presidential Directive – HSPD-7 – entitled “Critical Infrastructure Identification, Prioritization, and Protection", signed by President George W. Bush, on December 17, 2003, served to amplify the focus and attention on Critical Infrastructure Protection.
Terrorists seek to destroy, incapacitate, or exploit critical infrastructure and key resources across the United States to threaten national security, cause mass casualties, weaken our economy, and damage public morale and confidence.
America’s open and technologically complex society includes a wide array of critical infrastructure and key resources that are potential terrorist targets. The majority of these are owned and operated by the private sector and State or local governments. These critical infrastructures and key resources are both physical and cyber-based and span all sectors of the economy.
Critical infrastructure and key resources provide the essential services that underpin American society. The Nation possesses numerous key resources, whose exploitation or destruction by terrorists could cause catastrophic health effects or mass casualties comparable to those from the use of a weapon of mass destruction, or could profoundly affect our national prestige and morale. In addition, there is critical infrastructure so vital that its incapacitation, exploitation, or destruction, through terrorist attack, could have a debilitating effect on security and economic well-being.
While it is not possible to protect or eliminate the vulnerability of all critical infrastructure and key resources throughout the country, strategic improvements in security can make it more difficult for attacks to succeed and can lessen the impact of attacks that may occur. In addition to strategic security enhancements, tactical security improvements can be rapidly implemented to deter, mitigate, or neutralize potential attacks.
In response to this directive, seventeen CIP sectors of national importance were specified:
- Information technology
- Telecommunications
- Chemicals
- Transportation systems, including mass transit, aviation, maritime, ground/surface, and rail and pipeline systems
- Emergency services
- Postal and shipping services
- Agriculture, food (meat, poultry, egg products)
- Public health, health care, and food (other than meat, poultry, egg products)
- Drinking water and waste water treatment systems
- Energy, including the production refining, storage, and distribution of oil and gas, and electric power
- Banking and finance
- National monuments and icons
- Defense industrial base
The US Department of Energy (DOE) bears responsibility for leadership of the Energy sector, encompassing the production refining, storage, and distribution of oil and gas, and electric power except for commercial nuclear power facilities. DOE responsibilities in this sector include:
- collaboration with all relevant Federal departments and agencies, State and local governments, and the private sector, including with key persons and entities in their infrastructure sector;
- conducting or facilitating vulnerability assessments of the sector; and
- encouraging risk management strategies to protect against and mitigate the effects of attacks against critical infrastructure and key resources.
In June 2006, the U.S. Department of Homeland Security (DHS) announced completion of the National Infrastructure Protection Plan (NIPP) Base Plan, including a sector-specific plan for the Energy Sector. The Vision statement for the energy sector stated:
The Energy Sector envisions a robust, resilient energy infrastructure in which continuity of business and services is maintained through secure and reliable information sharing, effective risk management programs, coordinated response capabilities, and trusted relationships between public and private security partners at all levels of industry and government.
Relevant Systems
The following diagrams included in the Energy Sector plan highlight the components in the relevant systems addressed by this sector. Each of these sectors is highly dependent of information systems to administer and control complex, interconnected systems.
The descriptions accompanying each diagram came from the National Infrastructure Protection Plan (Energy Sector).
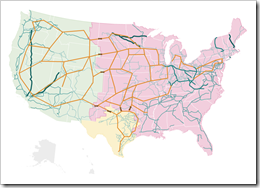
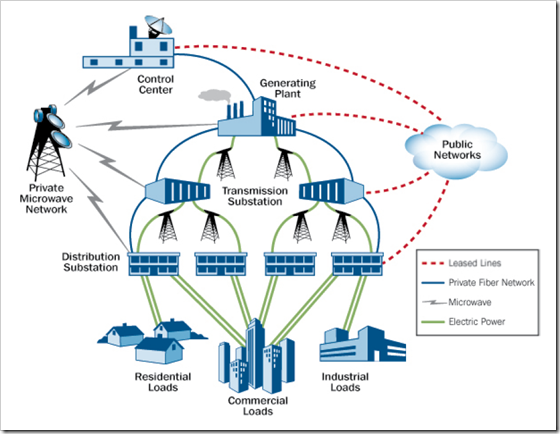
The electrical distribution grid
The U.S. electricity segment contains more than 5,300 power plants with approximately 1,075 gigawatts of installed generating capacity. Approximately 49 percent of electricity is produced by combusting coal (primarily transported by rail), 19 percent in nuclear power plants, and 20 percent by combusting natural gas. The remaining generation is provided by hydroelectric plants (7 percent), oil (2 percent), and by renewable (solar, wind, and geothermal) and other sources (3 percent). Electricity generated at power plants is transmitted over 211,000 miles of high-voltage transmission lines. Voltage is stepped down at substations before being distributed to 140 million customers over millions of miles of lower voltage distribution lines. The electricity infrastructure is highly automated and controlled by utilities and regional grid operators using sophisticated energy management systems that are supplied by supervisory control and data acquisition (SCADA) systems to keep the system in balance.
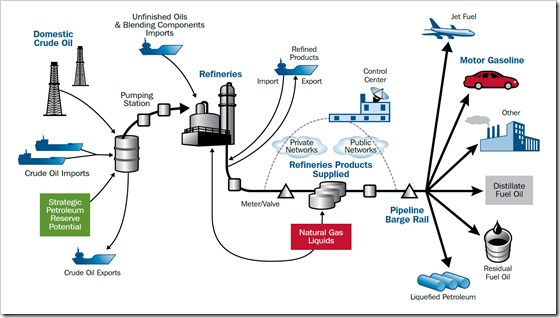
The Petroleum System
The petroleum segment entails the exploration, production, storage, transport, and refinement of crude oil. The crude oil is refined into petroleum products that are then stored and distributed to key economic sectors throughout the United States. Key petroleum products include motor gasoline, jet fuel, distillate fuel oil, residual fuel oil, and liquefied petroleum gases. Both crude oil and petroleum products are imported, primarily by ship, as well as produced domestically. Currently, 66 percent of the crude oil required to fuel the U.S. economy is imported. In the United States, there are more than 500,000 crude oil-producing wells, 30,000 miles of gathering pipeline, and 51,000 miles of crude oil pipeline. There are 133 operable petroleum refineries, 116,000 miles of product pipeline, and 1,400 petroleum terminals. Petroleum also relies on sophisticated SCADA and other systems to control production and distribution; however, crude oil and petroleum products are stored in tank farms and other facilities.
The Flow of Natural Gas
Natural gas is also produced, piped, stored, and distributed in the United States. Imports of liquefied natural gas (LNG) are increasing to meet growing demand. There are more than 448,000 gas production and condensate wells and 20,000 miles of gathering pipeline in the country. Gas is processed (impurities removed) at over 550 operable gas processing plants and there are almost 302,000 miles of interstate and intrastate pipeline for the transmission of natural gas. Gas is stored at 399 underground storage fields and 103 LNG peaking facilities. Finally, natural gas is distributed to homes and businesses over 1,175,000 miles of distribution pipelines. The heavy reliance on pipelines highlights the interdependency with the Transportation Sector and the reliance on the Energy Sector for power means that virtually all sectors have dependencies with the Energy Sector.
Interdependencies across the economy
Although the electricity, oil and gas sub-sectors are complex in and of themselves, we must also recognize that these systems interact with other key CIP sectors. The networked connectivity among these sectors amplifies increases the probability of an attack in one sector to directly affect multiple other sectors.
It is interesting to note that even small and medium size U.S. companies included in this interconnected network:
… are more and more exposed to cyber threats from organized crime, foreign intelligence services, and probably terrorist organizations; 85 percent of U.S. critical infrastructure is owned and operated by private companies — and these companies are especially vulnerable to determined attacks which may ruin or seriously disrupt company operations.… (source: Homeland Security Newswire: “Cyber threats now targeting traditional companiesâ€)
In recognition of the importance of addressing information security issues, the Energy sector plan states:
Today’s developing “information age†technology has intensified the importance of CIP, in which cyber security has become as critical as physical security to protecting energy CI/KR. The Energy Sector has rapidly responded to the increasing need for enterprise-level physical and cyber security efforts and business continuity plans. Voluntarily conducted vulnerability assessments have not only improved sector security but have also demonstrated industry commitment to a secure and resilient Energy Sector. Many asset owners and operators conduct self-assessments or contract with third parties to perform energy vulnerability assessments and implement protective programs at their facilities.
Specific efforts to address information security in the Electricity subsector include:
NERC has developed Cyber Security Standards CIP-002 through 009,37 which have been filed with FERC for approval and address the following requirements:
- Data and information classification according to confidentiality
- Identification and protection of cyber assets related to reliable operation of the bulk electric systems
- Process control, SCADA, and incident reporting
NERC’s CIPC has issued a summary of several electric power vulnerability assessment methodologies, including a variation of DOE’s Vulnerability and Risk Analysis Program methodology, in a suite of potential vulnerability assessment tools that electric power companies should consider using.
Specific work to address information security in the Oil and Natural Gas subsectors include:
Establishing goals for vulnerability identification, detection and response:
- Assess security vulnerabilities at single-point assets such as refineries, storage terminals, and other buildings, as well as networked features such as pipelines and cyber systems and
- Work toward resilient and secure cyber networks and SCADA systems to detect and respond to cyber attacks.
The AGA, the Interstate Natural Gas Association of America (INGAA), and APGA worked together to develop and release Security Guidelines: Natural Gas Industry, Transmission and Distribution. These guidelines provide an approach for vulnerability assessment, a critical facility definition, detection/deterrent methods, response and recovery guidance, cyber security information, and relevant operational standards. The industry security guidelines incorporate a risk-based approach for natural gas companies to consider when identifying critical facilities and determining appropriate actions, and are based on the DHS Homeland Security Advisory System (HSAS). The TSA, along with the PHMSA, is currently conducting onsite reviews based on these guidelines.
Importance of Energy Sector
So, just how important is the Energy Sector as a Critical Infrastructure? Though somewhat outdated, the 2006 DCSINT Handbook No. 1.02, Threats and Terrorism states:
Energy is the infrastructure that supplies the driving force in most of American life today. Energy of some kind heats our homes, moves us for one point to another and drives our businesses and industry. The energy sector is critical to the well being of our economy, national defense and quality of life. The sector is divided into to areas, electricity and oil/natural gas. Electricity is required to operate and maintain homes, hospitals, schools, businesses and industrial plants; it is also necessary to refine oil. Disruption of electrical flow or a power grid would impact the economy and defense as well as response and recovery. Natural Gas consists of three major components: exploration and production, transmission, and distribution, with the U.S. producing 20% of the world’s natural gas supply. Oil’s infrastructure consists of five components: production, crude oil transport, refining, product transport and distribution, and control and other external support systems. The thousands of miles of pipelines offer an endless list of targets for terrorist attacks, and during transport there are opportunities for impacting more than one critical infrastructure. Over 43% of the total U.S. oil refining capacity is clustered along the Texas and Louisiana coasts. This area is subject to natural attacks as well as those of terrorists.
…
Recently the oil industry occupied the headlines, and the criticality of this infrastructure is not lost on terrorists. In mid-December 2004, Arab television aired an alleged audiotape message by Usama bin Laden in which he called upon his followers to wreak havoc on the U.S. and world economy by disrupting oil supplies from the Persian Gulf to the United States. The U.S. uses over 20.7 million barrels a day of crude oil and products and imports 58.4% of that requirement. On 19 January 2006 al-Qaeda leader Osama bin Laden announced in a video release that, “The war against America and its allies will not be confined to Iraq…..â€, and since June of 2003 there have been 298 recorded attacks against Iraqi oil facilities. Terrorists conduct research as to the easiest point to damage the flow of oil or to the point where the most damage can be done.
Scenarios involving the oil fields themselves, a jetliner crashing into the Ras Tanura
facility in Saudi Arabia could remove 10 percent of the world’s energy imports in one
act. Maritime attacks are also option for terrorists; on October 6, 2002 a French tanker carrying 397,000 barrels of crude oil from Iran to Malaysia was rammed by an explosive laden boat off of the port of Ash Shihr, 353 miles east of Aden. The double-hulled tanker was breached, and maritime insurers tripled the rates. Energy most travel often long distances from the site where it is obtained to the point where it is converted into energy for use, a catastrophic event at any of the sites or along its route can adversely impact the energy infrastructure and cause ripples in other infrastructures. The security of the pipeline in Alaska increases in importance as efforts are made to make America more independent on energy use.
Securing Information and Control Systems
Of course, the business of oil and gas production and distribution relies heavily on security information management systems, the systems which control energy production and distribution represent widely points of access for potential cyber attacks.
In a report entitled, “21 Steps to Improve Cyber Security of SCADA Networks,†the US Department of Energy stressed the importance of security in control systems:
The U.S. energy sector operates the most robust and reliable energy infrastructure in the world. This level of reliability is made possible by the extensive use of Supervisory Control and Data Acquisition (SCADA), Distributed Control System (DCS), and other control systems that enable automated control of energy production and distribution. These systems integrate a variety of distributed electronic devices and networks to help monitor and control energy flows in the electric grid and oil and gas infrastructure.
Automated control has helped to improve the productivity, flexibility, and reliability of energy systems. However, energy control systems communicate with a multitude of physically dispersed devices and various information systems that can expose energy systems to malicious cyber attacks. A successful cyber attack could compromise control systems and disrupt energy networks and the critical sectors that depend on them.
Securing control systems is a key element in protecting the Nation’s energy infrastructure. The National Research Council identified "protecting energy distribution services by improving the security of SCADA systems" as one of the 14 most important technical initiatives for making the nation safer across all critical infrastructures.
In addition, the National Strategy to Secure Cyberspace states that "securing DCS/SCADA is a national priority".
Athough the NERC CIP standards apply specifically to electricity generation and distribution, the major categories could just as well apply to the Petroleum and Natural Gas subsectors:
- Identification and documentation of the critical cyber assets associated with the critical assets that support the reliable operation of the [oil or gas distribution system].
- Minimum security management controls in place to protect critical cyber assets.
- An appropriate level of personnel risk assessment, training, and security awareness for personnel having authorized cyber or unescorted physical access to critical cyber assets, including contractors and service vendors.
- Identification and protection of the electronic security perimeter(s) inside which all critical cyber assets reside, as well as all access points on the perimeter.
- Implementation of a physical security program for the protection of critical cyber assets.
- Defined methods, processes, and procedures for securing those systems determined to be critical cyber Assets, as well as the non-critical cyber assets within the electronic security perimeters.
- Identification, classification, response, and reporting of cyber security incidents related to critical cyber assets.
- Recovery plans for critical cyber assets that follow established business continuity and disaster recovery techniques and practices.
Recognized best practices for data security that are aligned with and answer the demands of these requirements include:
- Critical asset identification and documentation.
- Data classification.
- Encryption of data at rest and in transit.
- Data masking to hide information, for example, in test and development environments.
- Access control to assure robust identification, authentication and authorization of system users.
- Separation of duties to define administrative roles according to need.
- Privileged user access control, closely tied to separation of duties, allows administrators only that access required to perform their jobs.
- Database access monitoring, alerting and reporting.
- Change control and configuration management.
- Audit controls for all security processes.
Oracle Data Security Solutions
Oracle provides a wide range of information security products to meet the needs of industry requirements and information security best practices, including:
- Encryption (for data at rest and in transit)
- Data Masking
- Privileged Database User Access Control
- Identity and Role Administration
- Access Control
- Audit and Compliance Management
- Label Security
- Information Rights Management
In addition, complementary products from other vendors can be combined with the Oracle suite of products to implement a Defense-in-Depth Critical Infrastructure Protection security strategy strategy for the oil and gas industries.
Phew! That’s a lot of information from many sources. I hope you find this helpful.
A partial list of sources I used:
- Oracle White Paper: Protecting the Electric Grid in a Dangerous World
- Energy: Critical Infrastructure and Key Resources Sector-Specific Plan as input to the National Infrastructure Protection Plan (Redacted)
- North American Energy Reliability Corporation (NERC)
- NERC Critical Infrastructure Protection (CIP) cyber security standards
- Presidential Decision Directive NSC-63 on Critical Infrastructure Protection
- Homeland Security Presidential Directive – HSPD-7
- DHS Sector-specific plan for the Energy Sector
- National Infrastructure Protection Plan (Energy Sector)
- DCSINT Handbook No. 1.02, Threats and Terrorism
- 21 Steps to Improve Cyber Security of SCADA Networks
- National Strategy to Secure Cyberspace (February 2003)
Thanks for getting this far! If you have any input or suggestions, please submit a comment or drop me an email.

![image_thumb[8][1] image_thumb[8][1]](http://www.discoveringidentity.com/wp-content/uploads/2010/07/image_thumb81.png)
![image_thumb[10] image_thumb[10]](http://www.discoveringidentity.com/wp-content/uploads/2010/07/image_thumb10.png)