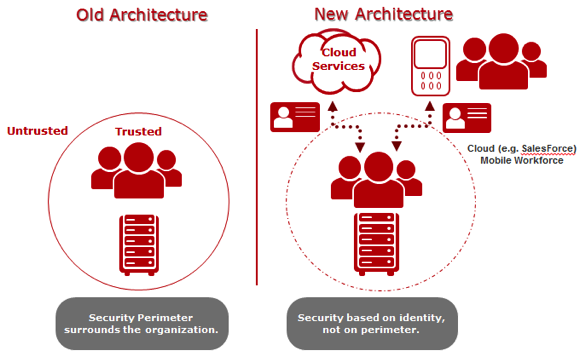
Yesterday, I was introduced to a recently-published 90+ page report, “The Report of the Commission on the Theft of American Intellectual Property.”
The Commission on the Theft of American Intellectual Property is an independent and bipartisan initiative of leading Americans from the private sector, public service in national security and foreign affairs, academe, and politics. The three purposes of the Commission are to:
- Document and assess the causes, scale, and other major dimensions of international intellectual property theft as they affect the United States
- Document and assess the role of China in international intellectual property theft
- Propose appropriate U. S. policy responses that would mitigate ongoing and future damage and obtain greater enforcement of intellectual property rights by China and other infringers
The members of this commission represent an interesting cross section of private and public sector leaders:
- Dennis C. Blair (co-chair), former Director of National Intelligence and Commander in Chief of the U. S. Pacific Command
- Jon M. Huntsman, Jr. (co-chair), former Ambassador to China, Governor of the state of Utah, and Deputy U. S. Trade Representative
- Craig R. Barrett, former Chairman and CEO of Intel Corporation
- Slade Gorton, former U. S. Senator from the state of Washington, Washington Attorney General, and member of the 9-11 Commission
- William J. Lynn III, CEO of DRS Technologies and former Deputy Secretary of Defense
- Deborah Wince-Smith, President and CEO of the Council on Competitiveness
- Michael K. Young, President of the University of Washington and former Deputy Under Secretary of State
The report addresses the huge scale of intellectual property theft – involving hundreds of billions of dollars and huge impact on ongoing innovation:
The scale of international theft of American intellectual property (IP) is unprecedented—hundreds of billions of dollars per year, on the order of the size of U. S. exports to Asia. The effects of this theft are twofold. The first is the tremendous loss of revenue and reward for those who made the inventions or who have purchased licenses to provide goods and services based on them, as well as of the jobs associated with those losses. American companies of all sizes are victimized. The second and even more pernicious effect is that illegal theft of intellectual property is undermining both the means and the incentive for entrepreneurs to innovate, which will slow the development of new inventions and industries that can further expand the world economy and continue to raise the prosperity and quality of life for everyone. Unless current trends are reversed, there is a risk of stifling innovation, with adverse consequences for both developed and still developing countries. The American response to date of hectoring governments and prosecuting individuals has been utterly inadequate to deal with the problem.
The report recommends several short, medium and long term remedies, including public policy, legislation, public/private cooperation and advances in cyber security technology and processes.
In the last category, I was interested to read the following observation (emphasis mine):
Even the best security systems using vulnerability-mitigation measures, including those with full-time dedicated operations centers, cannot be relied on for protection against the most highly skilled targeted hackers. A network exists in order to share information with authorized users, and a targeted hacker, given enough time, will always be able to penetrate even the best network defenses.
Effective security concepts against targeted attacks must be based on the reality that a perfect defense against intrusion is impossible. The security concept of threat-based deterrence is designed to introduce countermeasures against targeted hackers to the point that they decide it is no longer worth making the attacks in the first place. In short, it reverses the time, opportunity, and resource advantage of the targeted attacker by reducing his incentives and raising his costs without raising costs for the defender. Conceptual thinking about and effective tools for threat-based deterrence are in their infancy, but their development is a very high priority both for the U. S. government and for private companies.
The observation that “a perfect defense against intrusion is impossible,” is chilling. Â What is to be done?
The report’s recommendation to battle this challenge:
Encourage adherence to best-in-class vulnerability-mitigation measures by companies and governments in the face of an evolving cybersecurity environment. Despite their limited utility against skilled and persistent targeted hackers, computer security systems still need to maintain not only the most up-to-date vulnerability-mitigation measures, such as firewalls, password-protection systems, and other passive measures.
They should also install active systems that monitor activity on the network, detect anomalous behavior, and trigger intrusion alarms that initiate both network and physical actions immediately. This is a full-time effort. Organizations need network operators “standing watch†who are prepared to take actions based on the indications provided by their systems, and who keep a “man in the loop†to ensure that machine responses cannot be manipulated.
Organizations need to have systems—software, hardware, and staff—to take real-time action to shut down free movement around the house, lock inside doors, and immobilize attackers once the alarms indicate that an intrusion has started. Some government agencies and a few corporations have comprehensive security systems like this, but most do not.
The bottom line is that Intellectual Property espionage is a huge problem with no simple solutions. Â Technology alone cannot solve the problem. Â There are major social, political, economic and cultural challenges that must be addressed. But we in the information security business have our work cut out for us.