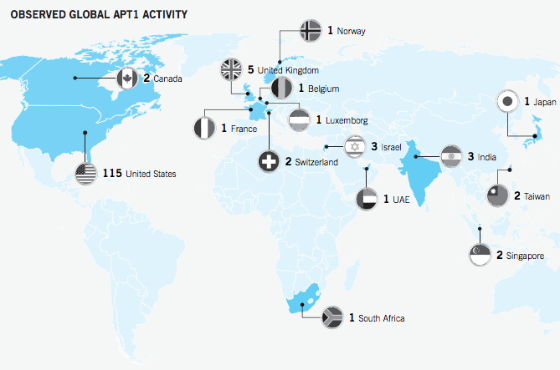
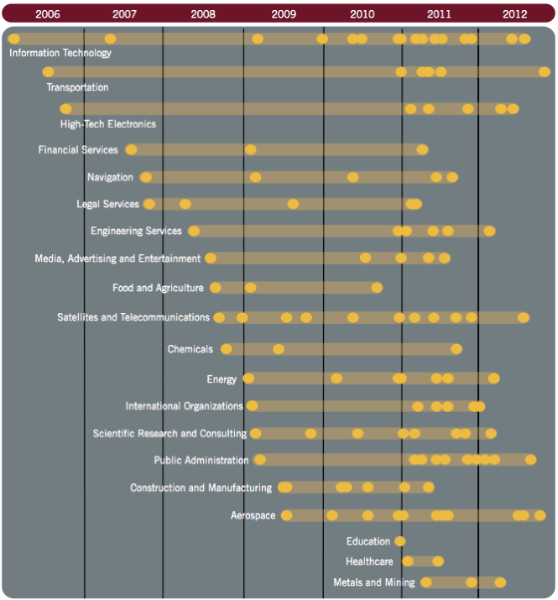
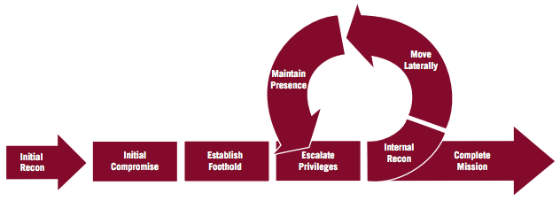
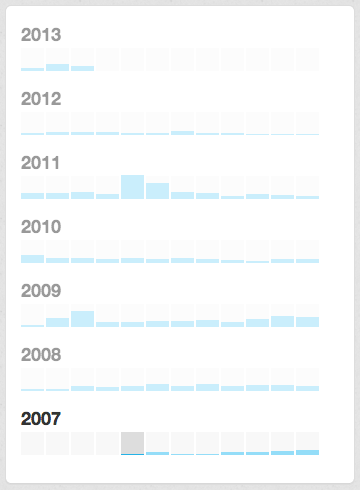
On the whiteboard in my office is a statement, “Abundance is born of shared ideas,” which I wrote down when first introduced to the book, “The Emergence of the Relationship Economy.” Â We don’t have to look very far to find many examples of how innovation sprang from ideas shared among creative, energetic people, leading to a rich abundance and growth of health, happiness or monetary wealth. Â This type of expansive thinking and action results when people look outside their situation in life, whatever it may be, and concentrate on what can be, rather than what is. Â This is an Abundance Mentality.
In contrast, a Scarcity Mentality prompts people to look inwardly, concentrating on the supposed constraints of a situation or condition in life. Â Perhaps this is no better illustrated that in a video being shared widely on Facebook. “9 Out Of 10 Americans Are Completely Wrong About This Mind-Blowing Fact.”
This video cleverly compares the wealth of the 1% richest people in the US with the rest of us 99 percenters. The graphics are well done, the narration and music are professional. Â However, there are at least five glaring errors in the supporting logic:
- By focusing on relative percentages rather than absolute values of personal wealth, the video infers that somehow the wealth of the 1% automatically diminishes the wealth of everyone else. Â After all, the stack of money for a guy on the left side of the chart sure looks smaller than the stack on the right side.
Â
- The video assumes scarcity, rather than abundance – that the sum of all society wealth or individual wealth is constrained to a fixed amount, that individuals are somehow limited in opportunity for growth because the 1% are insanely wealthy.
Â
- The video assumes that “fairness” is defined by a more even distribution of wealth.
Â
- The video infers that if some magic would occur to take the wealth of the 1% and spread it in some more equitable fashion across the rest of us, that we would all be more happy and the world would be a better place.
Â
- The video assumes that monetary wealth is the ultimate measure of success or happiness. Â After all, how can I be happy when someone else has more money than I do?
Â
With these comments, I don’t intend to excuse that rampant greed that fuels so much of society today, but I propose that getting all caught up in the “Scarcity Mentality” embodied in this video diminishes our ability to focus on innovative thought and action, which could alternatively lead to abundant growth, both individually and as a society.
Â
An example from my past is particularly important to me. Â I grew up on a small farm in southern Idaho. Â My college educated father loved farming, but couldn’t make enough money on the farm to support his growing family, so he began teaching school, an occupation he despised. Â We still worked on the farm, plowing ground, harvesting crops, feeding pigs and milking cows – tasks that demanded relentless attention but yielded little monetary gain. Â We never went on an overnight vacation; the cows demanded to be milked every morning and every night.
Â
But my dad had a vision of what his children could become.  Knowing that he couldn’t afford to send us to college, he allowed us to work outside the farm to earn money to finance our education.  I bucked a lot of hay, milked a lot of cows and made a lot of cheese for other employers.  Dad could have focused on the scarcity  and constraints of our farm and demanded that I exert all my work on the farm within those constraints, but he favored the abundant focus, which enabled me to get an education and pursue a successful career.  Dad never achieved even a modicum of monetary success that would show up in the video, but measures his abundance in the success, happiness and abundant lives of his seven children and their families.
Â
I recently watched a video where
Ben Carson told of how his mother, one of 24 children, abandoned by a bigamist husband, living in dire poverty, refused to focus on her own bad situation, but make her sons study at the public library so they could rise above the dire conditions in which they were born. Inspired by what he read, Ben rose to becomeÂ
Director of Pediatric Neurosurgery at Johns Hopkins Hospital. Â In addition to financial success, he has blessed many lives through his skill and dedicated service.Â
In my current employment, I could get all caught up in the fact that Larry Ellison has many more billions of dollars in his bank accounts than I have in mine, or that he has yet to invite me for dinner on his private Hawaiian island, or that I will never catch up to him monetarily. Â That would be Scarcity Mentality on my part. Â But when I focus on what I can do innovate, to serve our customers or to move our industry forward, opportunities blossom. That is the Abundance Mentality.
Â