Oracle Public Cloud Security
This morning, I read a recently published Oracle white paper, “Oracle Infrastructure and Platform Cloud Services Securityâ€:Â
This white paper focuses on shared and service-specific security capabilities of the following services: Oracle Compute Cloud Service, Oracle Storage Cloud Service, Oracle Network Cloud Service, Oracle Java Cloud Service, and Oracle Database Cloud Service – Enterprise Edition.
Oracle Cloud Services have been engineered from the ground up with security in mind.Â
Security is a top priority for Oracle Cloud solutions. Oracle’s vision is to create the most secure and trusted public cloud infrastructure and platform services for enterprises and government organizations. Oracle’s mission is to build secure public cloud infrastructure and platform services where there is greater trust – where Oracle customers have effective and manageable security to run their workloads with more confidence, and build scalable and trusted secure cloud solutions.
Development of Oracle cloud services follows a rigorous methodology for incorporating security into all aspects of cloud services:
The Oracle Cloud Services development process follows the Oracle Software Security Assurance (OSSA) program. The OSSA is Oracle’s methodology for incorporating security into the design, building, testing, and maintenance of its services. From initial architecture considerations to service post-release, all aspects of cloud services development consider security.
However, despite this solId foundation of security in the Oracle Public Cloud, it was interesting to read about the “shared responsibility model†for information security:
Oracle Cloud infrastructure and platform services operate under a shared responsibility model, where Oracle is responsible for the security of the underlying cloud infrastructure, and you are responsible for securing your workloads as well as platform services such as Oracle Database and Oracle WebLogic Server. The following figure shows the shared security responsibilities.
The following diagram provides a good illustration of the shared security model:
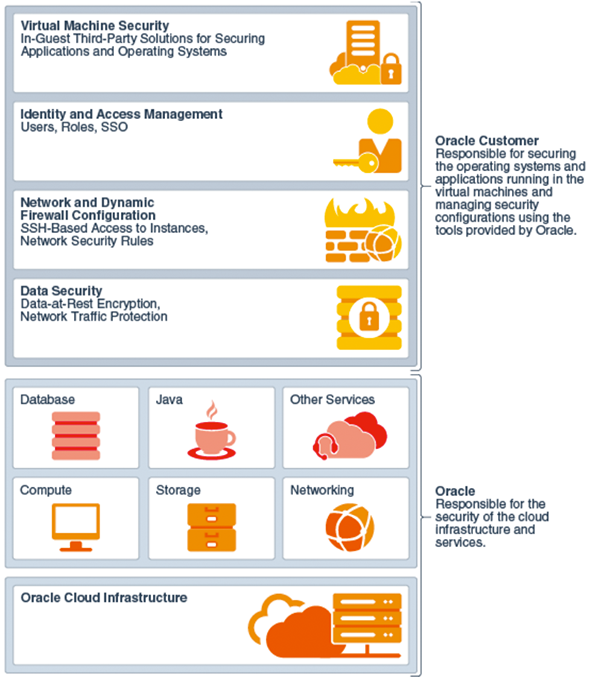
This illustrates how customers can’t just “throw things into the cloud,†and hope all will be well. There are significant responsibilities associated with deploying enterprise workloads in the cloud, even when the cloud services provide a highly secure foundation.