5 stages of data privacy grief
Do you want some tasty ice cream?  I think Tom Fishburne nailed the essence of why people put up with social media intrusion into their personal space.

Do you want some tasty ice cream?  I think Tom Fishburne nailed the essence of why people put up with social media intrusion into their personal space.

Stewardship: “the management or care of something, particularly the kind that works.†(Vocabulary.com)
I think my favorite new term in the business vernacular is “Data Stewardship.† I like how vocabulary.com emphasizes that good stewardship leads to things that work.
Extending the concept of stewardship to management of data, a recent article in AnalyticsIndia states:
One of the simplest definitions of data steward comes from the problem statement posed by authors Tom Davenport and Jill Dyché in their 2013 research study, ‘Big Data in Big Companies’:
“Several companies mentioned the need for combining data scientist skills with traditional data management virtues. Solid knowledge of data architectures, metadata, data quality and correction processes, data stewardship and administration, master data management hubs, matching algorithms, and a host of other data-specific topics are important for firms pursuing big data as a long-term strategic differentiator.â€
The article defines four major areas of responsibility for a data steward:
The third area in this list strikes particularly close to home. Â I like the fact that security and privacy are considered to be vital components of data stewardship. Â I firmly believe they make data work (as vocabulary.com suggests).
Has mis-use of surveillance and analytics technology become ingrained in our culture?  Not long ago, it was the NSA surveillance scandal the rocked our sensibilities.  Now Facebook and and Cambridge Analytics are in the forefront of public consciousness.  And what technology did Cambridge Analytica use to process the data taken from Facebook? Palantir – a data analytics company that claims “We believe in augmenting human intelligence, not replacing it.”
A somewhat chilling Bloomberg article, “Palantir Knows Everything About You,” the authors claim,
Peter Thiel’s data-mining company is using War on Terror tools to track American citizens. The scary thing? Palantir is desperate for new customers.
The article further explains:
Founded in 2004 by Peter Thiel and some fellow PayPal alumni, Palantir cut its teeth working for the Pentagon and the CIA in Afghanistan and Iraq. The company’s engineers and products don’t do any spying themselves; they’re more like a spy’s brain, collecting and analyzing information that’s fed in from the hands, eyes, nose, and ears. The software combs through disparate data sources—financial documents, airline reservations, cellphone records, social media postings—and searches for connections that human analysts might miss. It then presents the linkages in colorful, easy-to-interpret graphics that look like spider webs.
This leads to my favorite sentence from the article, “Everyone is a spidergram now.”
Imagine that you are at the center off a spidergram like the one for Peter Thiel, but that your relationships and connections are shown, not his. How would you like such information to be revealed?Â
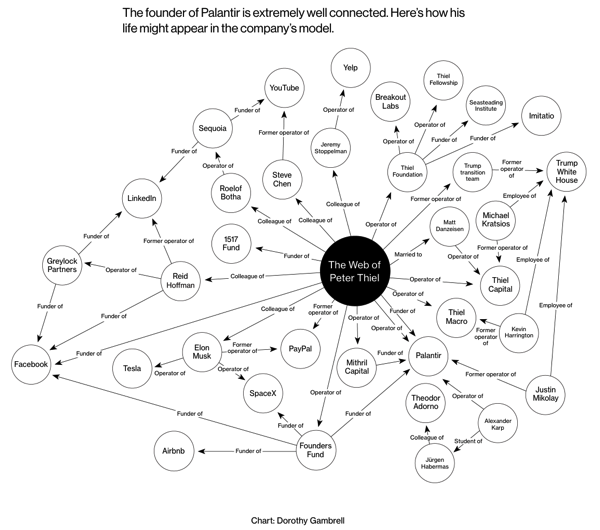
How is it possible that a company founded to help protect citizens of the United States could mis-use technology to spy on the very citizens it was supported to protect?
I think the article got it right, “The scary thing? Palantir is desperate for new customers.”
In my observation, any mis-use of technology can be traced directly to the desire for money or power, and often both. If we want to understand the motivation behind such mis-use, just remember the famous words of Rod Tidwell (Cuba Goodiing, Jr.) in the film Jerry Maguire …
In the wake of the US Senate grilling Mark Zuckerberg about the Cambridge Analytics scandal, and as we move ever so quickly towards the May 25th date when the EU will begin enforcing the General Data Protection Regulation (GDPR), it is easy to focus on the responsibilities online companies have for implementing what GDPR calls “Data Protection by Design and by Default.”
All that focus is good, but we should not forget the responsibilities each person has for making sure their own personal data is safe. In her blog post today, Emma Firth of digi.me proposes “10 ways to keep your personal data safe online.”
Please take a few minutes to read Emma’s commentary, but here are the ten points she recommends:
Thanks, Emma, for your insightful reminders.
And remember, in the words of Sergeant Phil Esterhaus (Michael Conrad) of Hill Street Blues fame …

This morning, I reviewed a proposal for improving a company’s security against data breach.  The main reasons giving for the investment in security technology were:
These are all valid reasons for making the proposed investment, but shouldn’t there be more? Doesn’t good security support good business results in a positive way?
By happy coincidence, just before I reviewed the proposal, I read a thought-providing article, “Reframing Cybersecurity As A Business Enabler,†published by Innovation Enterprise.  The introductory paragraph states the obvious:
Innovation is vital to remaining competitive in the digital economy, yet cybersecurity risk is often viewed as an inhibitor to these efforts. With the growing number of security breaches and the magnitude of their consequences, it is easy to see why organizations are apprehensive to implement new technologies into their operations and offerings. The reality is that the threat of a potential attack is a constant.
But rather than dwelling on the problem, this article challenges traditional thinking:
Though the threat is real, instead of viewing cybersecurity in terms of risk, organizations should approach cybersecurity as a business enabler. By building cybersecurity into the foundation of their business strategy, organizations will be able to support business agility, facilitate organizational operations and develop consumer loyalty.
The article explores each of these three business value areas in more detail. I have included a brief excerpt in each area:
Security supports business agility
Instituting strong security measures enables organizations to operate without being compromised or slowed down. Companies that invest in cyber resilience will be better able to sustain operations and performance – a definite competitive advantage over those caught unprepared by an attack.
Security facilitates business productivity
One survey of C-level executives revealed that 69% of those surveyed said digitization is ‘very important’ to their company’s current growth strategy. 64% also recognized that cybersecurity is a ‘significant’ driver of the success of digital products, services, and business models.Â
Security develops customer loyalty
PricewaterhouseCoopers’ 21st Global CEO Survey found that 87% of global CEOs say they are investing in cybersecurity to build trust with customers.Â
I recognize the need for strengthening security defense mechanisms for the sake of risk mitigation. However, if we restrict ourselves to the traditional “security as insurance policy†mindset, we are missing the greater value of good information security in supporting positive business success.Â

Technology has come a long way since my time time growing up on a small dairy farm in Idaho. A recent AP News article asks: “Is the world ready for cows armed with artificial intelligence?“
Answering its own question, the article observes:
No time to ruminate on that because the moment has arrived, thanks to a Dutch company that has married two technologies — motion sensors and AI — with the aim of bringing the barnyard into the 21st century.
The Dutch company, Connecterra offers a system, “The Intelligent Dairy Farmer’s Assistant (IDA),†to monitor individual cows and predict how to deal with problems that may arise.
IDA uses a motion-sensing device attached to a cow’s neck to transmit its movements to a program driven by AI. The sensor data, when aligned repeatedly with real-world behavior, eventually allows IDA to tell from data alone when a cow is chewing cud, lying down, walking, drinking or eating.
Those indicators can predict whether a particular cow is ill, has become less productive, or is ready to breed — alerting the farmer to changes in behavior that might otherwise be easily missed.
Back in the day, my Dad knew each of his cows well, and called each of them by name. Â However, modern dairies may have thousands of cows, not just a few dozen we had on our farm. Technology like IDA can really extend the ability of a dairy farmer to maximize production from all of the cows.
It does my heart good to see AI and IoT technologies applied to boost agribusiness.

History often plays interesting tricks in my mind.  For some reason, I had just assumed that calculus had been around far longer than any institution on this side of the proverbial pond.  But no - Harvard University was founded in the United States in 1636, several years before Isaac Newton and Gottfried Wilhelm Leibniz developed the foundations of calculus.
A Harvard University article, “Which Came First: Harvard or Calculus?â€, published last year, confirmed this interesting bit of history.

Justifying investment in security technology is tough. Because it is difficult to measure ROI for Security controls, many companies justify security investments in terms of risk reduction.
Recognizing this difficulty, Slavik Markovic, CEO of Demisto, proposes “10 best practices for bolstering security and increasing ROI.†He introduces the topic in part, with this statement:
CISOs are being asked to provide proof that the money spent [on security] — or that they are asking to be spent — will lead to greater effectiveness, more efficient operations or better results.
Rather than proposing a specific ROI calculation method, Markovic recommends taking a more holistic approach to the problem. Â His recommended 10 best practices are:
I recommend that you read the commentary supporting each best practice.
Two of these recommendations entail leveraging technology to expand the expertise and capabilities of security professionals, rather than relying on just hiring more expensive staff:
3. Automate and orchestrate. Strive for security orchestration and process automation. The current threat landscape is vast, complex and constantly changing. Even a well-staffed security operations center cannot keep pace with the volume of alerts, especially with the ever-increasing number of duplicates and false positives. Use automation for threat hunting, investigations and other repetitive tasks that consume too much of analysts’ time.
6. Leverage analytics. Adopt advanced analytics. Machine learning and artificial intelligence are delivering truly innovative solutions. CISOs should research these two fields carefully to determine which analytics tools best fit their agencies, taking into account the organization’s strengths and weaknesses related to skills, personnel and risks.
I like the way Markovic looks broadly at how to justify security investment. Â Security, after all, touches almost every aspect of modern business, and is strategically vital to business success.
When I give a presentation about the Global Data Protection Regulation (GDPR), someone usually asks how long it will be before the United States has a similar regulation?  I really don’t know, but the Senate Facebook hearings last week show that the topic is certainly on the minds of our elected leaders.

Another strong indicator that a US regulation is forthcoming is the emergence of “GDPR-like†regulations in other countries.  For example, the article “A paradise for data privacy advocates – Bermuda’s privacy law now in full effect,†states:
With enactment of the Personal Information Protection Act (PIPA), Bermuda can now count itself among the ever-expanding list of jurisdictions with enhanced privacy protections. PIPA, passed on July 27, 2016, and entered into force in December 2017, shares many of the more stringent requirements and protections with Europe’s impending General Data Protection Regulation (GDPR), which indicates a growing, global trend towards stepped-up privacy regimes.Â
Regulations such as this will put pressure on the US to act, in order to facilitate economic interaction with other countries:
Unless and until the United States passes an overarching privacy statute providing comparable levels of protection over the use of one’s personal information, including for non-US Persons, it is unlikely that the Privacy Commissioner will allow for the free flow of personal information between Bermuda and the United States.
A concluding statement
Ultimately, the trend towards greater privacy protections—and the limitation on cross-border data transfers, especially to the United States—is only picking up steam, as this Bermuda law highlights. And more may still be to come.
How soon do you think the United States will act?

This morning, I was delighted to finally download and read the new “Oracle and KPMG – Cloud Threat Report 2018.† I have known this was coming for a few months, but was delighted by how it turned out.  The report contains a wealth of timely, insightful information for those who need to know how to not only cope, but excel, in the rapidly changing information systems infrastructures of modern business.
Mary Ann Davidson, CSO, Oracle Corporation, stated in the report’s Foreword:
In the age of social media, it is popular to speak of what’s “trending.†What we are seeing is not a trend, but a strategic shift: the cloud as an enabler of security.
The dazzling insights in the Oracle and KPMG Cloud Threat Report, 2018 come not from professional pundits, but from troops in the trenches: security professionals and decision makers who have dealt with the security challenges of their own organizations and who are increasingly moving critical applications to the cloud.
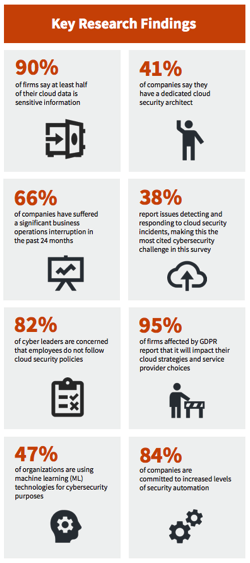
A few key research findings are summarized in the following list and illustrated by the numbers the “Key Research Findings” chart:
KPMG offers this Call to Action:
C-level, finance, HR, risk, IT, and security leaders are responsible for ensuring that the organization has a cybersecurity program to address risks inherent in the cloud.
Beyond making sure that risks are mitigated and compliance requirements are addressed, leaders should accept and assert their responsibility for protecting the business. A critical first step is to understand the “shared responsibility†principles for cloud security and controls. Knowing what security controls the vendor provides allows the business to take steps to secure its own cloud environment.
To further protect an organization, it is crucial that everyone in the organization—not just its leaders—is educated about the cloud’s inherent risks and the policies designed to help guard against those risks. This requires clear communication and training to employees on cloud usage. KPMG and Oracle’s research found that there may be considerable room for improvement in this area, as individuals, departments, and lines of business within organizations are often in violation of cloud service policies.
I have really just skimmed the report. Â I look forward to digesting the content more completely. Â Stay tuned for more analysis and commentary from my perspective.