Today I read an informative paper published by GigaOM Research entitled, “The Internet of Things: A Market Landscape.”  I find The Internet of Things to be the most interesting area of technology and business in my professional world today.  This paper did an excellent job of providing an overview of the IoT landscape and highlighting both opportunities and challenges.
A few things that I found intriguing:
IoT is not just new technology:
The internet of things is not a single technology trend. Rather, it is a way of thinking about how the physical world at large and the objects, devices, and structures within it are becoming increasingly interconnected.
The market is moving rapidly to mind-boggling scale:
- Some 31 billion internet-connected devices will exist by 2020, according to Intel.
- A family of four will move from having 10 connected devices in 2012 to 25 in 2017 to 50 in 2022.
- Mobile subscriptions will exceed the number of people in the world by early 2014.
Identity is first on the list of important characteristics:
For things to be manageable, they need to be identifiable either in terms of type or as a unique entity. … Identification by type or by instance is fundamental to the internet of things.
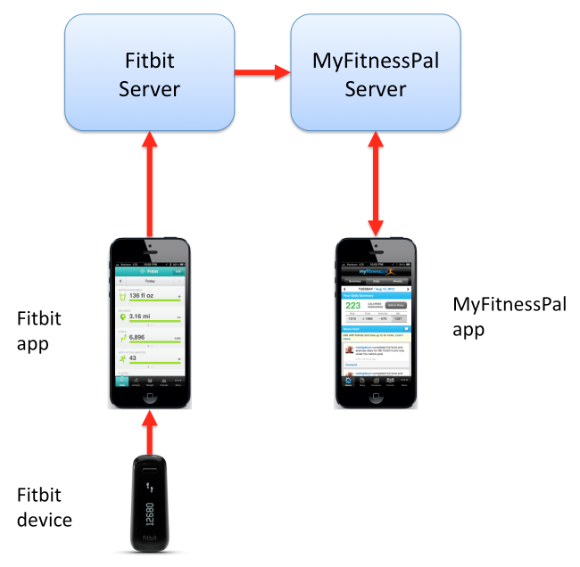
The power of IoT comes from connectivity, not just individual components:
The internet of things is an ultra-connected environment of capabilities and services, enabling interaction with and among physical objects and their virtual representations, based on supporting technologies such as sensors, controllers, or low-powered wireless as well as services available from the wider internet.
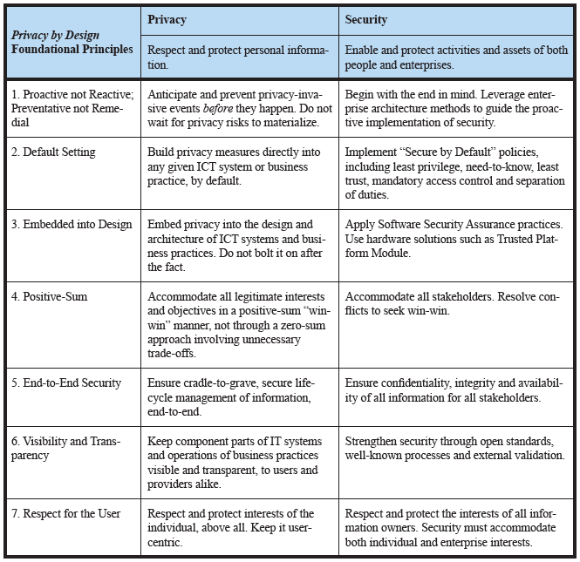
The biggest challenges? Â Security, monitoring and surveillance:
Computer security, say the experts, boils down to protecting the confidentiality, integrity, and availability of both data and services. With the internet of things looking set to create all manner of data, from heart rate and baby monitors to building management systems, there is clearly going to be a great deal to protect. …
The internet of things enables the whole world to be monitored. …  the potential for the inappropriate use of such technologies — for example, to spy on partners or offspring — will grow. In the business context as well, the role of the internet of things offers a wealth of opportunity but also of abuse.
The bottom line? Â The possibilities are vast, the challenges daunting, but IoT is happening. Â It will be great to go along for the ride.