Privacy by Design Ambassador
It was an honor today to be announced as a Privacy by Design Ambassador by the Information and Privacy Commissioner of Ontario, Canada:
Privacy by Design Ambassadors are an exclusive, but growing, group of privacy thought-leaders committed to ensuring the ongoing protection of personal information by following the Principles of PbD. Â Ambassadors advance the case for embedding privacy protective measures in technology, processes and physical design. …
The Information and Privacy Commissioner of Ontario (IPC) is an independent officer of the Legislature whose mandate is to oversee compliance with public sector access and privacy legislation and health sector privacy legislation in the province of Ontario.
The IPC recognizes ambassadors based on their attestations that they apply the principles of Privacy by Design. The IPC does not endorse any company or product of any recognized ambassador.
It was humbling to be listed among others whom I admire and respect for their contributions to the industry we serve.
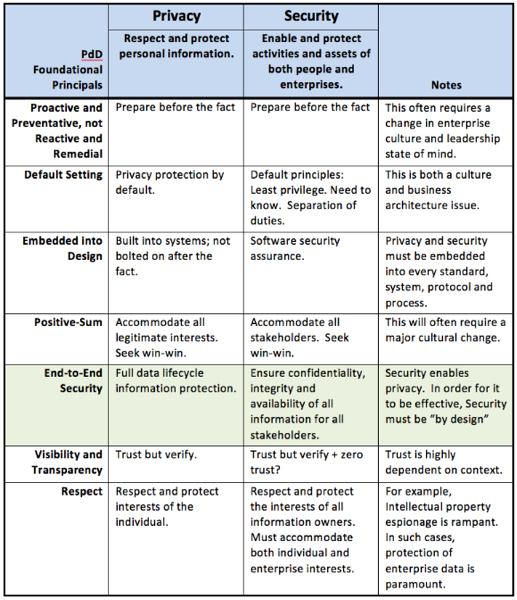
I have deeply appreciated the opportunity to work closely with Dr. Ann Cavoukian and her staff on a soon to be announced joint paper on principles of privacy and security. Â I look forward to announcing and discussing this paper soon.