Report: Mitigating Insider Threats
 A colleague referred me today to a long, but very useful technical report, “Common Sense Guide to Mitigating Insider Threats, 4th Edition,” published in December 2012 by the CERT® Program at Carnegie Mellon University. The report abstract states:
A colleague referred me today to a long, but very useful technical report, “Common Sense Guide to Mitigating Insider Threats, 4th Edition,” published in December 2012 by the CERT® Program at Carnegie Mellon University. The report abstract states:
This fourth edition of the Common Sense Guide to Mitigating Insider Threats provides the most current recommendations of the CERT® Program (part of Carnegie Mellon University’s Software Engineering Institute), based on an expanded database of more than 700 insider threat cases and continued research and analysis. It introduces the topic of insider threats, explains its intended audience and how this guide differs from previous editions, defines insider threats, and outlines current patterns and trends. The guide then describes 19 practices that organizations should implement across the enterprise to prevent and detect insider threats, as well as case studies of organizations that failed to do so.
It was interesting to read how the patterns and trends that they team observed indicated four classes of malicious insider activity:
- IT sabotage—an insider’s use of IT to direct specific harm at an organization or an individual
- theft of IP—an insider’s use of IT to steal IP from the organization. This category includes industrial espionage involving outsiders.
- fraud—an insider’s use of IT for the unauthorized modification, addition, or deletion of an organization’s data (not programs or systems) for personal gain, or theft of information that leads to an identity crime (e.g., identity theft or credit card fraud)
- miscellaneous—cases in which the insider’s activity was not for IP theft, fraud, or IT sabotage
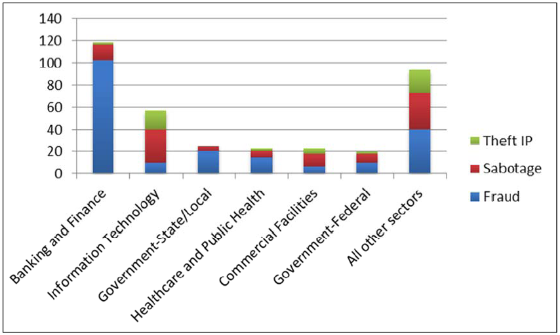
The following chart shows the top six infrastructure sectors for the three most important classes: Fraud, Sabotage, and Theft of IP:
The nineteen practices that are include in the report are:
- Consider threats from insiders and business partners in enterprise-wide risk assessments.
- Clearly document and consistently enforce policies and controls.
- Incorporate insider threat awareness into periodic security training for all employees.
- Beginning with the hiring process, monitor and respond to suspicious or disruptive behavior.
- Anticipate and manage negative issues in the work environment.
- Know your assets.
- Implement strict password and account management policies and practices.
- Enforce separation of duties and least privilege.
- Define explicit security agreements for any cloud services, especially access restrictions and monitoring capabilities.
- Institute stringent access controls and monitoring policies on privileged users
- Institutionalize system change controls
- Use a log correlation engine or security information and event management (SIEM) system to log, monitor, and audit employee actions
- Monitor and control remote access from all end points, including mobile devices.
- Develop a comprehensive employee termination procedure
- Implement secure backup and recovery processes
- Develop a formalized insider threat program
- Establish a baseline of normal network device behavior
- Be especially vigilant regarding social media
- Close the doors to unauthorized data exfiltration.
All in all, it is a very insightful and helpful report.