Identity
Author:
Mark Dixon
Thursday, January 28, 2010
3:47 pm
Last Thursday, January 21st, I gave a presentation at the Sun Horizons conference, “Healthcare Integration Through a New Perspective.†The title of my talk was “Identity Management: Securing Information in the HIPAA Environment.†I explored how the complementary functionality of Identity Management and Master Patient Index technologies can enable effective Patient Consent Management, a vital requirement for online health information networks.
A copy of my presentation deck is available for download here.
At the heart of my the presentation was the following diagram, which illustrates major components required in a Patient Consent Management system:
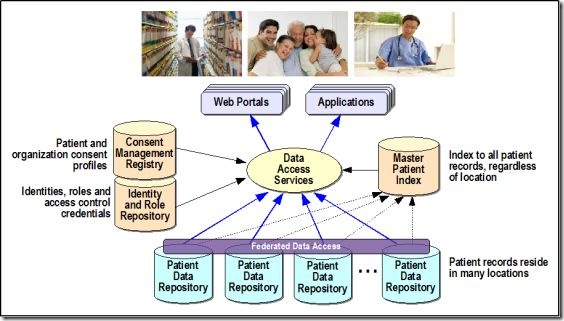
A brief explanation of key components follows:
Identity and Role Repository
IAM technology and methods provide the foundation for an effective patient consent management system. An Identity and Role Repository contains Identities, roles and access control credentials necessary to support the consent system. This repository includes:
- Patients
- Providers
- Access Rights
- Roles (map business responsibilities to access rights)
- Override Rights (Only users with specific roles can perform override without consent)
Consent Registry
A consent registry is required to specify what permissions have been granted by patients, within the allowable limits specified by each applicable jurisdiction. Some of the key attributes include:
- Consent Permissions for
- Patients
- Organizations
- Users
- System-wide mask (everyone)
- Fine gained access
- Include or exclude attributes
- Accommodation for multiple jurisdictions
Master Patient Index
A Master Patient Index enables correlation of patient data across multiple repositories. This is essential because patient records are typically help in multiple locations. In other cases, if patient records exist in the same physical data warehouse, they are often logically separated.
Federated Data Access
If patient data is located in physically or logically separate locations, Federated data access controlled allows access across domain boundaries without compromising the privacy or integrity of individual patient record repositories.
Data Access Services
By providing a set of centralized data access services governed by IAM, the Consent Registry and the Master Patient Index, a secure method of patient data access is possible.
 I had a conversation with a colleague this morning about the tension between two sales approaches:
I had a conversation with a colleague this morning about the tension between two sales approaches: