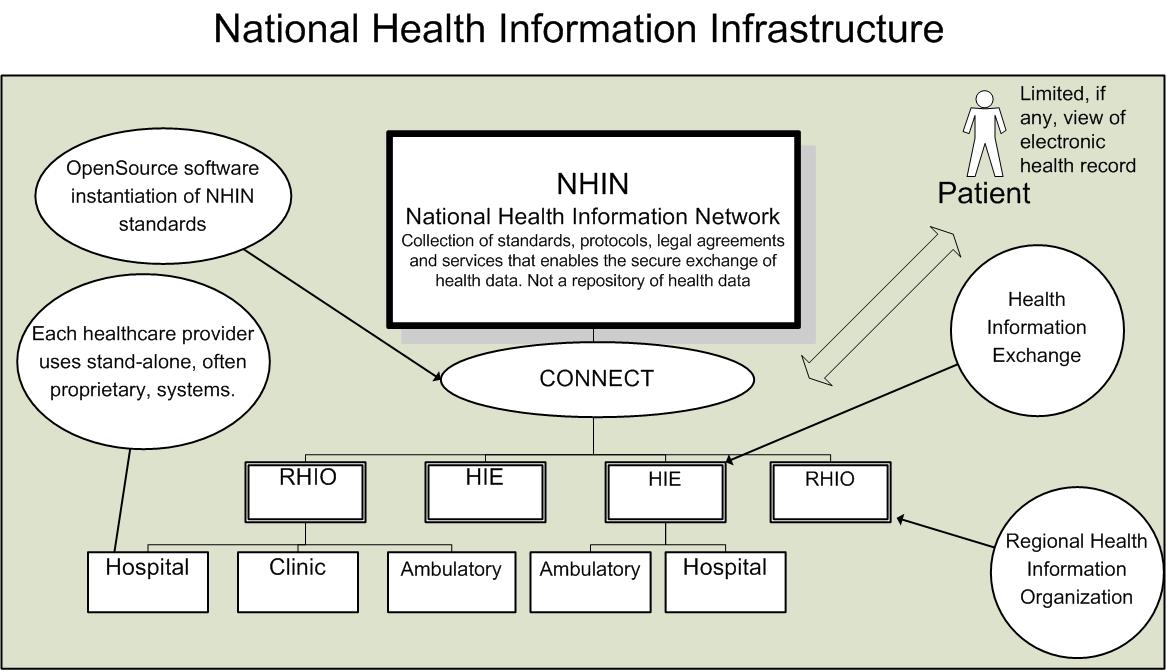
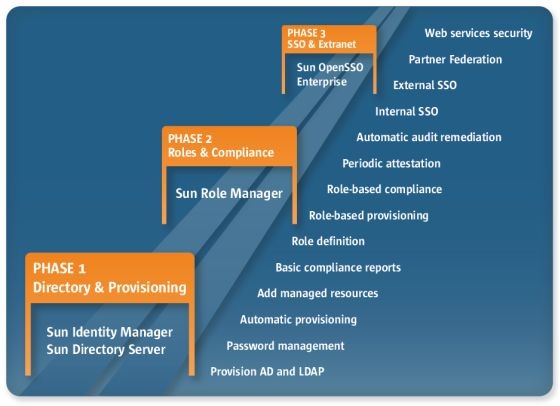
Identity
Author:
Mark Dixon
Tuesday, November 24, 2009
1:48 am
 I read a disturbing article by Dan Schwab of Fox Chicago News this morning entitled “Probe: ID rules lax at Chicago airports.†Perhaps the fact that I will board my 13th flight segment in two and a half weeks this afternoon fueled my interest in the article, which reported “a Fox Chicago News investigation discovered a major loophole at TSA checkpoints at O’Hare and Midway.â€
I read a disturbing article by Dan Schwab of Fox Chicago News this morning entitled “Probe: ID rules lax at Chicago airports.†Perhaps the fact that I will board my 13th flight segment in two and a half weeks this afternoon fueled my interest in the article, which reported “a Fox Chicago News investigation discovered a major loophole at TSA checkpoints at O’Hare and Midway.â€
During the past two months, Fox flew multiple employees – male, female, black, white, and Muslim – to different destinations around the country on different airlines.
The only requirement: They were not allowed to bring a photo ID. No passport. No driver’s license.
On every occasion, these Fox employees were allowed through security without a hitch as long as they showed that the name on their boarding pass matched the name on a couple of credit cards, according to Fox Chicago News.
Credit cards for identification? What happened to the requirement of a photo ID? This shows a remarkable lack of TSA compliance with recommended policy:
The federal Sept. 11 Commission’s final report included 10 pages that focused solely on the issue of terrorism and identity fraud. The report states: “Travel documents are as important as weapons. Fraud is no longer just a problem of theft. At many entry points to vulnerable facilities, including gates for boarding aircraft, sources of identification are the last opportunity to ensure that people are who they say they are.†…
By checking credit cards rather than a photo ID, TSA simply was following its own rules, which vaguely state that passengers without an acceptable ID will have to provide “information†to verify their identity, according to Fox Chicago News.
I’m not a big fan of the TSA. To me, it is at best a huge, bumbling bureaucracy, and at worst, a huge, oppressive police force. I really don’t feel safer because of them. However, regardless of my feelings, this is a clear example about how poorly executed identity policy can lead to easily exploited security breaches, even as a false aura of safety is provided for the law-abiding majority, who obediently shed shoes and jackets, empty pockets and briefcases, and subject themselves to humiliating searches while many obvious loopholes remain.
Just one example … next time you go through the TSA screening process, notice how closely (or not) airport employees’ ID badges are examined.
Happy trails!
PS. The Dave Granlund cartoon reminds me of the time I brought exercise weights with me on a trip. My luggage was manually searched every time – on each of four flight segments that week. I now keep those dastardly weights safely at home with my horribly dangerous one-inch pocket knife. Bitter? Nah!
 Today, I imported all entries from the Discovering Identity blog from blogs.sun.com into my WordPress blog at DiscoveringIdentity.com. I believe that I will have more flexibility in publishing my blog and associated content using the WordPress publishing engine than was available on the Roller site.
Today, I imported all entries from the Discovering Identity blog from blogs.sun.com into my WordPress blog at DiscoveringIdentity.com. I believe that I will have more flexibility in publishing my blog and associated content using the WordPress publishing engine than was available on the Roller site.![]() If you care to follow my postings on the new site, please bookmark the RSS feed.
If you care to follow my postings on the new site, please bookmark the RSS feed.