Identity Hardness – Do You Need Talc or Diamonds?
I had an interesting Twitter conversation recently with @steve_lockstep and @NishantK about Identity Assurance.  It began with Steve’s comment about how Facebook identities were of little worth, unfit to use with valuable transactions.  Nishant suggested that most Relying Parties (RP’s) are content with “soft” identities that have to with personal likes and interests, while significantly fewer RP’s rely on “hard” identities.
Nishant’s observation about “hard” and “soft” identities made me think of the Mohs Mineral Hardness Scale, which assigns an “absolute” hardness value to different minerals. Â Wikipedia’s article uses the following table to illustrate this concept:
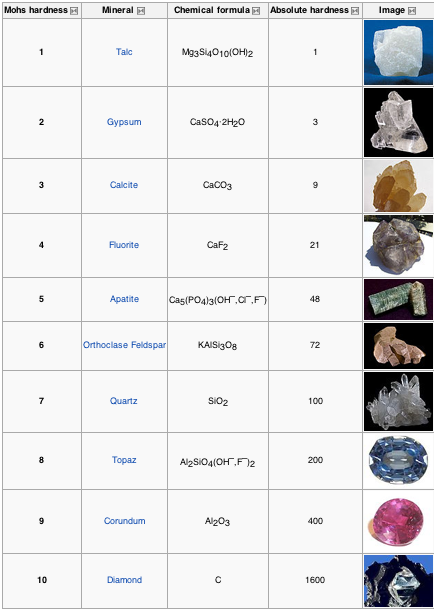
Perhaps we could suggest a corresponding mineral and hardness value to each of NIST’s standard four Levels of Assurance (LOA) shown in the following table.
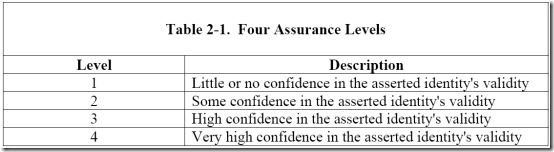
Steve stated on Twitter that “I’m preoccupied with hard identity: doctors, lawyers, bank accts, patients”: scenarios where Facebook just doesn’t work. We could say that Steve is dealing in diamonds (level 4), but Facebook only offers talc (level 1).  Having a tangible example helps illustrate the somewhat ethereal LOA concept.  And over time, perhaps we can come up with a more definitive way to measure just how hard a particular Identity Assurance process really is.
As a parting thought: I have suggested minerals match NIST Assurance Levels 1 and 4. Â What would you suggest for the other two?

Thanks Mark for the interesting analogy and discussion!
A property that goes with hardness is brittleness. Soft minerals and identities are malleable, but hard ones do not bend. Once a ‘diamond’ identity is issued in a certain context, it’s no good for any other context. When we look in detail at hard identities like the professional credentials of doctors and lawyers, we see that they don’t “interoperate”. These sorts of identities have unbending ‘crystaline’ registration processes, usage rules, rights and liabilities. I argue that LOA is irrelevant in describing them. If a doctor’s ID were LOA 4, that fact doesn’t tell us anything at all about their aptness to participate in non-health related LOA 4 transactions. If the one person is both a doctor and a lawyer, they need to get themselves two completely separate ‘diamond’ hard identities, and use them in the respective silos.
Is it possible that I could have a “master” hard identity with subordinate identities or personas that were equally as well vetted? Using your example, it would be possible for one person to have both doctor credentials and lawyer credentials, each with their own licensing and assurance process, but still be tied to the same master identity.
I myself don’t see the obvious benefit. To reach agreement on the specification of a master ID, we would need to get all the RPs together and satisfy their authentication needs. And then once a master were in place, all the RPs would need to modify their registration processes and their transaction processing to make use of it. There are untold legal complexities in businesses and professional bodies shifting their membership processes to use a new externally issued master ID.
I have put up an untested hypothesis that the total cost of a master ID would exceed the combined costs of the historically siloed, sovereign IDs; see http://lockstep.com.au/blog/2011/02/02/tco-multiple-ids.
Calling PhD students!