Security and Compliance in the Cloud
This morning, I listened to an excellent webinar entitled “Pinning Down Cloud Computing,†hosted by Yankee Group Research. Yankee Group Vice President Camille Mender and Senior Analyst Agatha Poon explored the popular topic of cloud computing, focusing much on the business details enterprises must pay attention to if they are to successfully harness the promises of cloud computing – important things like uptime/availability, maintenance, penalties for non-performance, limitations of liability and privacy / data protection, to name a few.
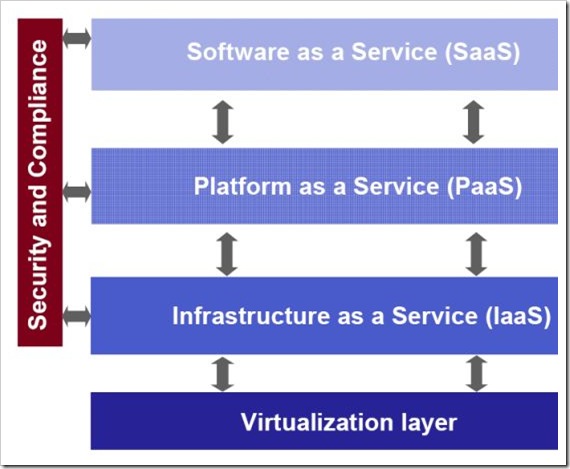
I liked the following diagram used to discuss the different levels or tiers of a cloud “stack†architecture. The “Security and Compliance†bar to the left is a good way to illustrate the importance of information security and related compliance activities at each tier of the stack. Of course, Identity Management is a critical underpinning of that security and compliance functionality.
 (Diagram Copyright © 2009 Yankee Group Research, Inc. All rights reserved. Used with permission.)
(Diagram Copyright © 2009 Yankee Group Research, Inc. All rights reserved. Used with permission.)
It was pointed out that the top three barriers to cloud computing uptake are:
- Security (39%)
- Reliability (35%)
- IT governance (33%)
The cloud computing market is still maturing. So far, only a small percentage of enterprises are shifting a large part of their IT budgets to the cloud. Recognizing the essential role Identity Management plays in security and governance is critical to accelerating that movement.
