Identity
Author:
Mark Dixon
Friday, February 15, 2013
6:18 am
In the book “The Emergence of the Relationship Economy,” Jay Deragon proposes that:
The value of the relationship is categorized into four elements of the individual, and may be of one dimension or a combination.:
- Economic
- Intellectual
- Emotional
- Spiritual
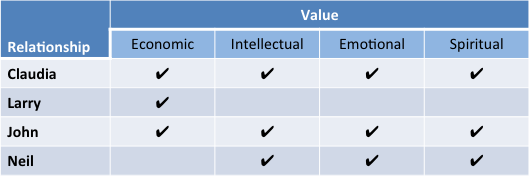
To understand the juxtaposition of Identity and Relationship, I listed some of my current relationships in the following tables:
Â
People Relationships
Â
The first table lists a few people relationships I have.  The first, my wife, provides value to me (that sounds kind of crass, actually) in all areas.  Her economic value comes not from revenue (she chose dual careers as  Homemaker and Stay-at-home-Mom), but in her thrift, wise use of money and sound economic advice.  In addition, I deeply value her wisdom, friendship and spirituality.
My relationship with Claudia is in quite stark contrast to my very distant relationship with my employer, Larry Ellison. Â Sorry, Larry, I see the value of our relationship as primarily economic, although I must admit receiving a bit of intellectual stimulation from reading about your personal exploits.
On the other hand, my relationship with John, a colleague at Oracle, began as an economic relationship as we worked together in the sales organization, but grew into a deep friendship, with intellectual, emotional and spiritual value.
The final example is Neil, the Bishop of our church congregation and close neighbor.  We have developed a  friendship I value highly, based on strong spiritual, emotional and intellectual relationships.
It could be an interesting experience to assess the value we receive from all of the people with whom we interact in some way, but the real purpose of this post is to explore the value of relationships with information systems. Â The following table illustrates a few of the systems with which I interact regularly.
Â
System Relationships
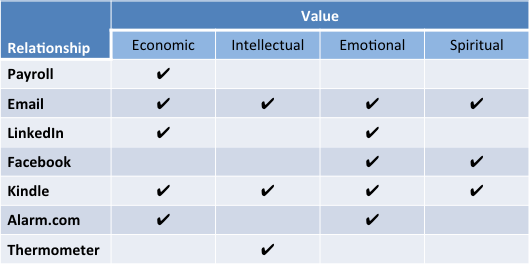
Â
I definitely have an economic relationship with Oracle Payroll. Â Twice every month, a nice paycheck drops into my bank account, and I log onto the payroll system to see how much money I pay in taxes and investments. Â While I admit to deriving some emotional satisfaction from that process, we’ll let it remain as an economic value.
In contrast, the different email systems I use can provide value across the board, as I communicate with people on a wide range of subjects.
In social networks, LinkedIn is the vehicle I use to primarily keep track of professional colleagues and associates, although I get emotional value out of maintaining and building friendships with people across miles and time.
Facebook, on the other hand, is where I actively seek to strengthen emotional and spiritual ties with friends and family.
Kindle also sweeps the board – my virtual bookshelf contains titles that provide value in all four areas.
This brings me to a couple of examples of my relationship with “things” that deliver value. Â I can monitor and control my new home alarm system from an app on my phone. Â The system provides economic protection and emotional peace of mind.
Finally, my remote thermometer satisfies an intellectual curiosity about how hot it is outside, here in the Arizona desert.
It is important to note that how a person uses or views a particular system may influence the value he receives. Â For example, I know of people who leverage Facebook primarily for economic advantage. Â I just choose not to do that.
Â
So What?
How does this relate (pun intended) to Identity? Â Here are a few thoughts:
- Exposed Personae: Certainly different facets of my personal identity are exposed as I interact with different people. Â Larry Ellison will never see (even if he cared to) parts of my personality that I have reserved for my closest friends. Â My closest friends will never know of parts of myself I share only with my wife.
- Context: The context of relationships differ, depending on time of day, distance apart, frequency of interaction, mutual interests, etc. Â Such differing context has a large impact on the value derived from relationships.
- Connection method:  How does the relationship connect me with the person or system?  With people, is the relationship primarily in person, by phone, via email, via  a social network or all of these?  Is a digital identity required to enable the relationship?
- Available functionality: For systems with which I interact, what functionality is available? Â What can the system deliver that delivers value to me?
- Authorized access: Of the sum of all functionality in a system, what am I authorized to use, or what functions do I choose to use?
Focus on Value
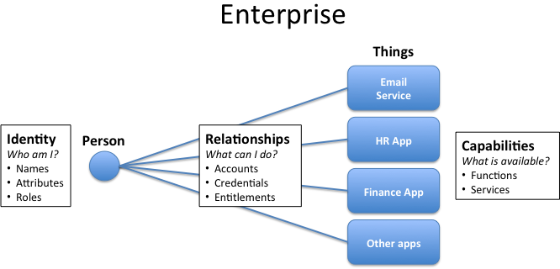
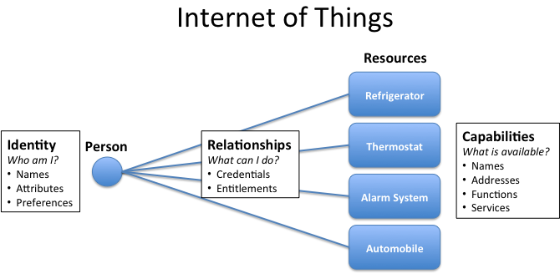
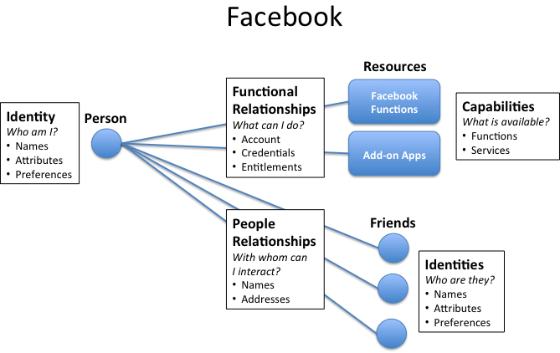
Yesterday’s post illustrated a few cases of how relationships can exist between identities and resources or identities and people. Â I propose that we should focus not which relationships exist, but on what value can be derived from each relationship. Â
In interpersonal relationships, hopefully, value flows to both parties. Â In the case of employee relationships with enterprise systems, hopefully value accrues both to the employee and employer. Â In the case of individuals connecting to online systems or things, hopefully each person receives value from those relationships.
And Identity is at the core of making these relationships happen.
Stay tuned …
Â
Â
Â





 Â