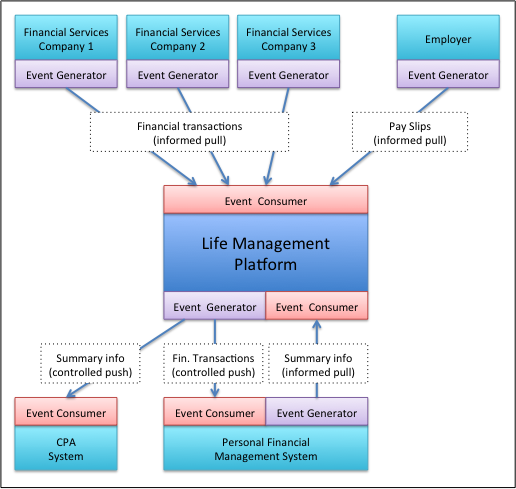
 I have been intrigued by the potential emergence of “Life Management Platforms” as described in the Kuppinger-Cole advisory note, “Life Management Platforms: Control and Privacy for Personal Data.” The concept that particularly interests me is integration between systems that would allow controlled sharing of information, using principles Martin Kuppinger describes as “informed pull” and “controlled push.”
I have been intrigued by the potential emergence of “Life Management Platforms” as described in the Kuppinger-Cole advisory note, “Life Management Platforms: Control and Privacy for Personal Data.” The concept that particularly interests me is integration between systems that would allow controlled sharing of information, using principles Martin Kuppinger describes as “informed pull” and “controlled push.”
Life Management Platforms are far more than Personal Data Stores. They not only support a secure store for sensitive personal information. They allow making a better use of that information. The real value lies in the sharing of that information supported by Life Management Platforms. …
These concepts are like two sides of the same coin. Furthermore they are the essence of why Life Management Platforms are far more than just a store of personal data. Storing personal data is just a little piece of the value proposition of Life Management Platforms. And just sharing this information by allowing some parties to access it without further control and without keeping a grip on that data is also not what really makes a Life Management Platform. That would be nothing more than a social network with some better access control capabilities.
The key capability of Life Management Platforms is the ability for exactly the two concepts mentioned. This is about using new types of privacy-aware apps which allow making use of sensitive information in a way that provides value to the owner of that sensitive information.
I can think of dozens of ways this could immediately help me in my life, in addition to the many that Martin included in his report. For example:
- Twice each month, I download an electronic copy of my payslip and manually transcribe key bits of information from that unstructured report into the money management program on my personal computer. Wouldn’t it be great if I could do an “informed pull” of that information in a way that would automatically transfer selected data from my employer to my money management program, just like I do from my bank and credit card vendors?
- Each year, I assemble a bunch of information to give to my accountant to prepare my tax return. Wouldn’t it be great I could use a “controlled push” of such information from my computer to his?
- I recently visited a new dentist. Wouldn’t it be great if I could have used use a “controlled push” of my profile and medical history to their system, rather than fill out yet another set of paper forms?
- We recently had a great time with all of our six children and their families at a family reunion in the White Mountains of Arizona. Wouldn’t it have been great to post addresses and lodging details once and let each member of the family do an “informed pull” that automatically populated their mobile phone calendars, address books and GPS units?
And the list of possibilities could go on and on. Many industries could benefit from this concept – healthcare, financial services, travel, hospitality and many more.
I like some of the emerging systems from vendors Martin mentions, but each has its challenges.
As its name suggestions, Personal.com is a useful application for storing personal information. In its current state, it is kind of like Evernote for structured data – an ability to put personal data into secure “gems” that can have any number of attributes, and have those gems available either on a website or on my mobile phone. It has the ability to share gems with other personal.com members or with non-members via email (if you dare use that insecure medium). However, personal.com lacks the structured data exchange between applications that is essential for the use cases I mentioned above. It even suffers from a disturbing lack of data exchange internally. For example, if I fill in a business card “gem” with my name and contract information, that data isn’t available to help me fill in somewhat related gems, such as passport, drivers license or social security card gems.
I like the concepts behind connect.me. Reputation is indeed an important attribute of my identity. However, I haven’t found a practical use in my life for the service or something like it. Having a way to use “controlled push” of my reputation to consuming applications may make it more useful. But I am definitely monitoring their progress, and patiently awaiting their new product launch.
I have enjoyed reading through the QIY website – particularly about their efforts to forge relationships with companies that are interested in working with personal data in an integrated way. Unfortunately for me, a life-long mono-linquist, I don’t know the enough Dutch words to sign up for the QIY consumer website.
So, it is great to see progress in this area. What the Life Management Platform concept really needs to move forward is definition and demonstration of a set of open, secure APIs to implement “informed pull” and “controlled push” information sharing capabilities for real. Then, personal data platforms and related applications that produce and consume structured data while protecting both privacy and personal control could flourish.



 Today, the 11g R2 version of the Oracle Identity and Access Management platform was
Today, the 11g R2 version of the Oracle Identity and Access Management platform was 