Arizona Broadband Map: I live in a DSL-free Zone!
 Several years ago, I was a regular participant in the Arizona Telecommunications and Information Council (ATIC), and still receive interesting information from that group from time to time. This week, I received a link to the “Arizona Broadband Map“. This map was produced as a result of a federal grant to the Arizona Government Information Technology Agency (GITA):
Several years ago, I was a regular participant in the Arizona Telecommunications and Information Council (ATIC), and still receive interesting information from that group from time to time. This week, I received a link to the “Arizona Broadband Map“. This map was produced as a result of a federal grant to the Arizona Government Information Technology Agency (GITA):
The U. S. Congress has appropriated $7.2 billion to develop broadband in the U. S. for unserved and underserved areas.
…
This funding includes grants for broadband infrastructure, computer centers, sustainable projects that promote broadband use; and grants to the states for broadband planning and for mapping broadband in their respective states to use in the creation a national broadband map.
…
The broadband mapping project will collect and verify the availability, speed and location of broadband across Arizona. This information will be publicly available; updated on a semi-annual basis through 2011. Citizens, local governments, and related research organizations will enjoy a direct benefit from access to this new and additional information.
The following image is a snapshot of the highest level of the interactive map for Arizona:
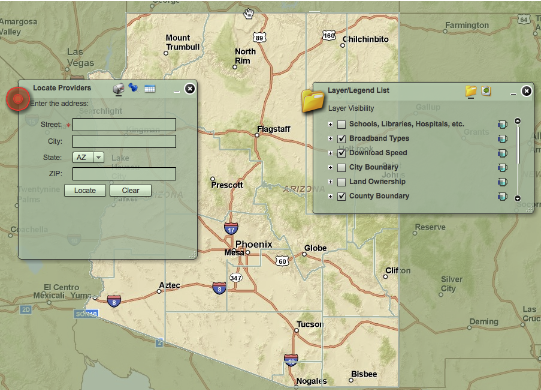
A really interesting bit of information appeared when I specified my home address and chose the DSL coverage map. The pink shade in the following image shows areas with DSL broadband coverage. The tan area shows my subdivision – an DSL-free island in a sea of coverage in Mesa, AZ.
I knew that we couldn’t get DSL from Qwest. I just didn’t know how localized the problem was, and still don’t know why it is this way. According to this map, my neighbors on the other side of the street can choose DSL, while I cannot.
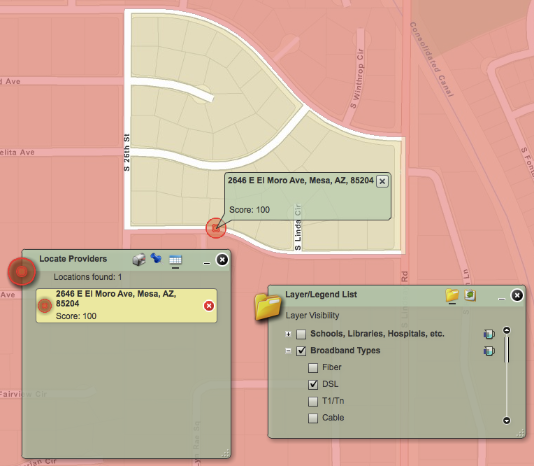
It is nice to know that our home is part of the “underserved” broadband area targeted by this study.
Perhaps this is just a symptom of the Cox Communications monopolistic conspiracy! Or more probably, an oversight in Qwest planning.
Thanks, GITA, for providing this insight.

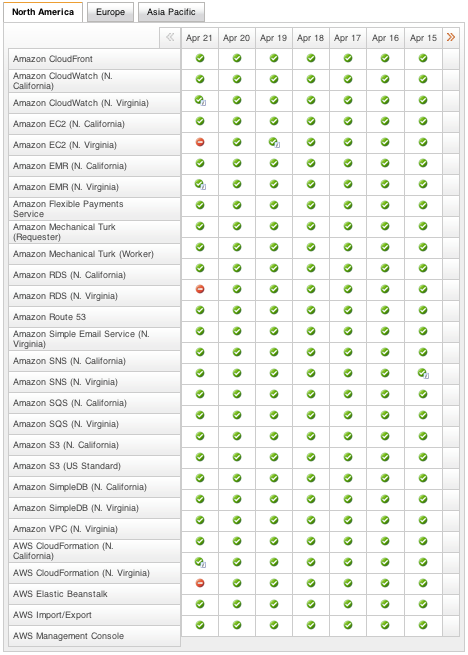
 As failures in Amazon’s Cloud Services (reported by
As failures in Amazon’s Cloud Services (reported by 
 Thanks to my colleague
Thanks to my colleague  I am anxious for the time when I can buy groceries or pay for a meal with my iPhone. According to Juniper Research, that time may be be closer than you would think.
I am anxious for the time when I can buy groceries or pay for a meal with my iPhone. According to Juniper Research, that time may be be closer than you would think.
 I was pleased to receive the following notice from Oracle product management in my email box this week:
I was pleased to receive the following notice from Oracle product management in my email box this week: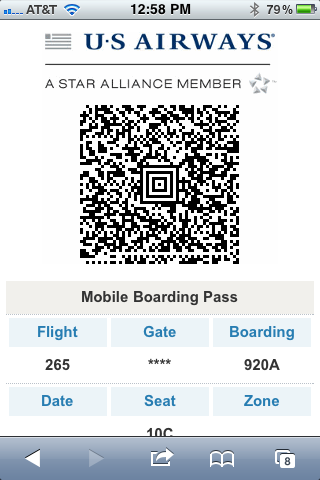 We road warriors often grouse about the dumb stuff the airlines do and the weirdness of the TSA. However, once in awhile, we can cheer about a big step forward in flying convenience. The latest cheerable enhancement is the paperless boarding pass. Other airlines have offered this perk for awhile, but US Airways has offered the option for the just the past few weeks. I gingerly brought both paper and paperless boarding passes for a flight week before last, but today, I didn’t even bring a paper backup.
We road warriors often grouse about the dumb stuff the airlines do and the weirdness of the TSA. However, once in awhile, we can cheer about a big step forward in flying convenience. The latest cheerable enhancement is the paperless boarding pass. Other airlines have offered this perk for awhile, but US Airways has offered the option for the just the past few weeks. I gingerly brought both paper and paperless boarding passes for a flight week before last, but today, I didn’t even bring a paper backup.
 As I search for a decent blog editor, I am re-visiting ScribeFire, a brower extension which I used back in the Windows days before I found LiveWriter. It seems to do a decent job, but I can’t find support for Technorati tags or Twitter messaging. Image management is limited.
As I search for a decent blog editor, I am re-visiting ScribeFire, a brower extension which I used back in the Windows days before I found LiveWriter. It seems to do a decent job, but I can’t find support for Technorati tags or Twitter messaging. Image management is limited.  A real surprise for me when migrating recently from Window to Mac is the dearth of good blogging clients on MacOS. I have tried
A real surprise for me when migrating recently from Window to Mac is the dearth of good blogging clients on MacOS. I have tried